stormous volkswagen ransomware claim
Here is a quick reality check from the world of cyber threat intel:
According to some criminals, they had broken into Volkswagen internal systems and were threatening to leak car data unless VW paid up.

Immediately, some CTI feeds and infosec accounts started reporting that a group called Stormous had hacked Volkswagen.
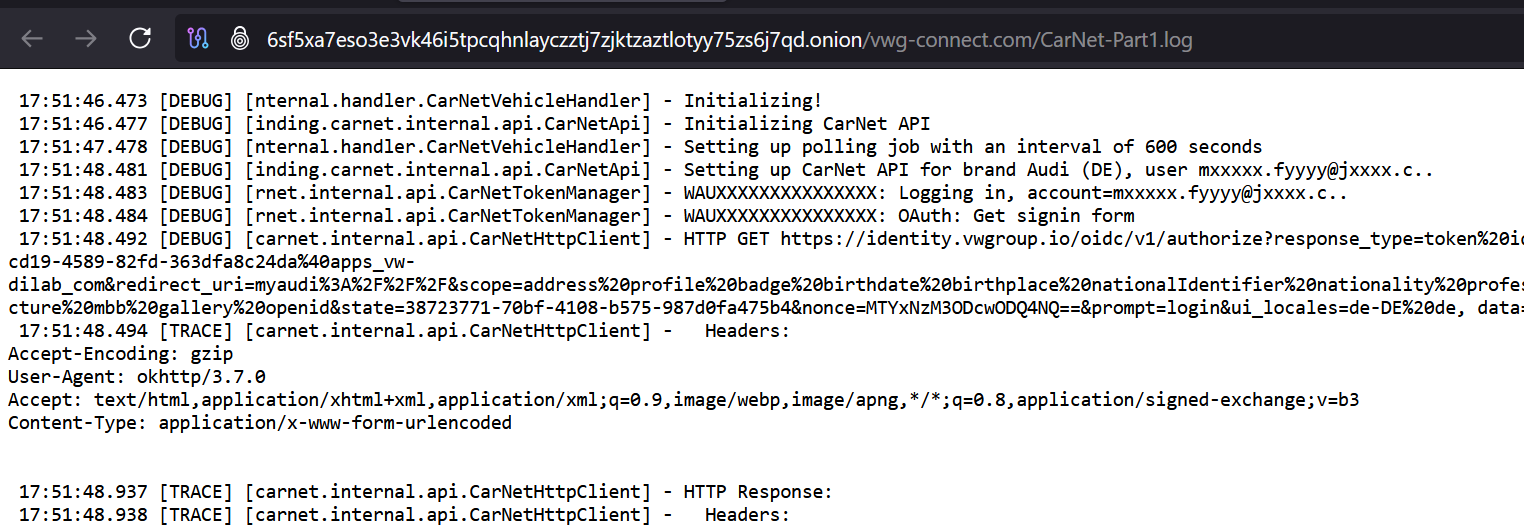
To prove it, they dropped a file called “CarNet-Part1.log” - a file with what looked like authentication logs and access tokens. The implication was: we are in your systems, pay us.
But here is the thing:
That data didn’t come from an internal Volkswagen system.
Their sample is just debug output from a smart home system - data someone had publicly posted on a forum while troubleshooting their own setup. Nothing proprietary. Nothing secret. Just some user sharing their own logs (somewhat anonymized, sorry Markus - you should remove these logs, they pinpoint your home address pretty clear).
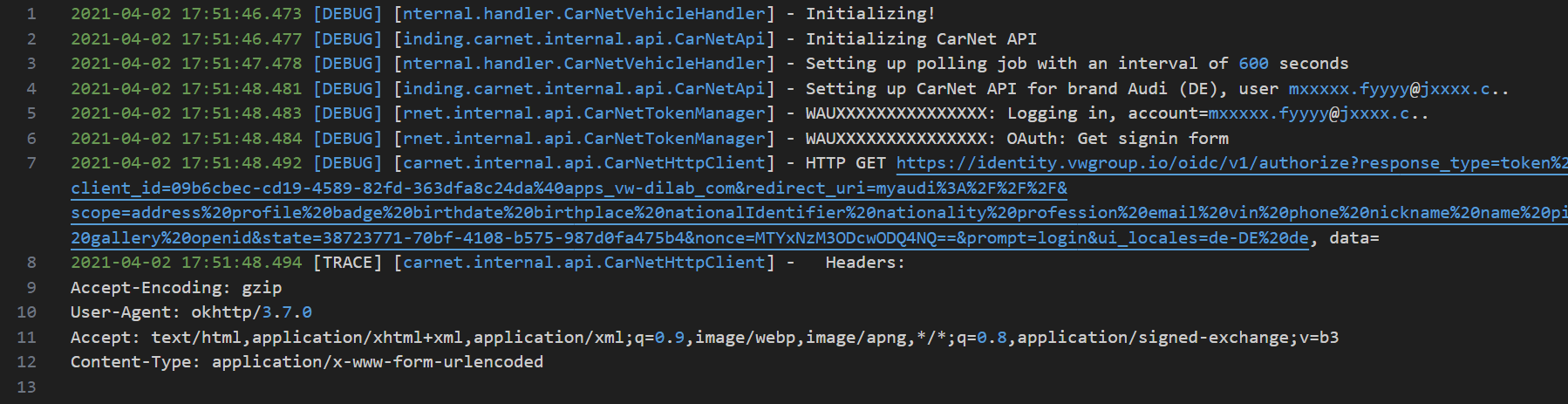
Stormous even edited the timestamps to hide how old the file was. They stripped out the year to make it look fresh. Classic misdirection.
The takeaway?
Criminals lie.
They fake hacks, doctor files, and hype things up just to get attention or cash. The fact that a group says they hacked someone doesn’t mean they did. Their blog post isn’t evidence. So when something like this pops up, don’t just repeat it. Check it. Context matters. And not every screenshot with access_token in it is a breach.
Let’s stop giving criminals free PR. kthxbye.
Update 2025-06-06
Unfortunately, more and more media outlets are now picking up the story - without verifying the claims. Every headline amplifying these falsehoods adds weight to a story that never had legs to begin with. To their credit, at least some journalists have reached out to Volkswagen for comment - but asking for a statement doesn’t undo the damage of running with a baseless story in the first place. Just because something sounds dramatic doesn’t mean it is real. Journalists and editors should apply some level of skepticism especially when dealing with claims from threat actors who thrive on manipulation and attention.
Don’t let sensationalism do their job for them.