trojan
 | Released | 2025-05-15 |
| Retired | 2025-10-16 | |
| Author | MrManj |
Scenario
Task 01
Question: What is the build version of the operating system?
For this purpose, a Windows memory image memory.vmem is available, as well as various disk artifacts in the form of an AD1 archive and a packet capture from 2023-05-30 covering the period between 06:49:56 and 07:01:08. To get an overview of the system at the time of the memory dump, MemProcFS is used in the following.
MemProcFS.exe -forensic 4 -f .\memory.vmem -license-accept-elastic-license-2-0
Initialized 64-bit Windows 10.0.19041
============================== MemProcFS ==============================
- Author: Ulf Frisk - pcileech@frizk.net
- Info: https://github.com/ufrisk/MemProcFS
- Discord: https://discord.gg/pcileech
- License: GNU Affero General Public License v3.0
---------------------------------------------------------------------
MemProcFS is free open source software. If you find it useful please
become a sponsor at: https://github.com/sponsors/ufrisk Thank You :)
---------------------------------------------------------------------
- Version: 5.14.12 (Windows)
- Mount Point: M:\
- Tag: 19041_7476824a
- Operating System: Windows 10.0.19041 (X64)
==========================================================================
[FORENSIC] Forensic mode completed in 19s.
Answer: 19041
Task 02
Question: What is the computer hostname?
In the mounted image, there is a folder named sys containing various files that hold information about the system.
Get-Content M:\sys\computername.txt
DESKTOP-38NVPD0
Answer: DESKTOP-38NVPD0
Task 03
Question: What is the name of the downloaded ZIP file?
Assuming that the downloaded file is still located in the users Downloads folder, the second artifact package disk_artifacts.ad1 can be mounted and analyzed using FTK Imager.
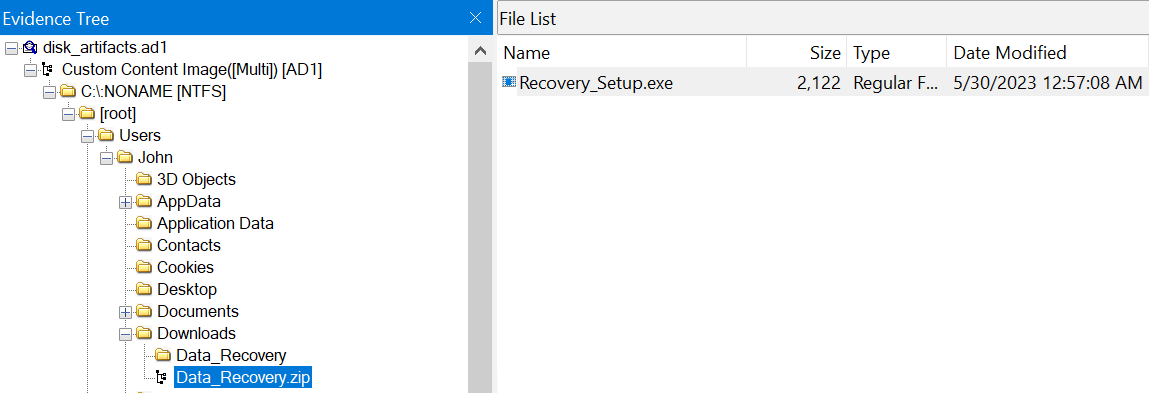
Answer: Data_Recovery.zip
Task 04
Question: What is the domain of the website (including the third-level domain) from which the file was downloaded?
To trace the downloads and their origin, the file C:\Users\John\AppData\Local\Microsoft\Edge\User Data\Default\History can be exported from the previously used artifact collection. This file contains the browser history in SQLite3 format. Using an appropriate query, downloads and their sources can be filtered.
SELECT
downloads.target_path,
datetime((downloads.start_time/1000000) - 11644473600, 'unixepoch') as "time",
downloads.tab_url
FROM
downloads
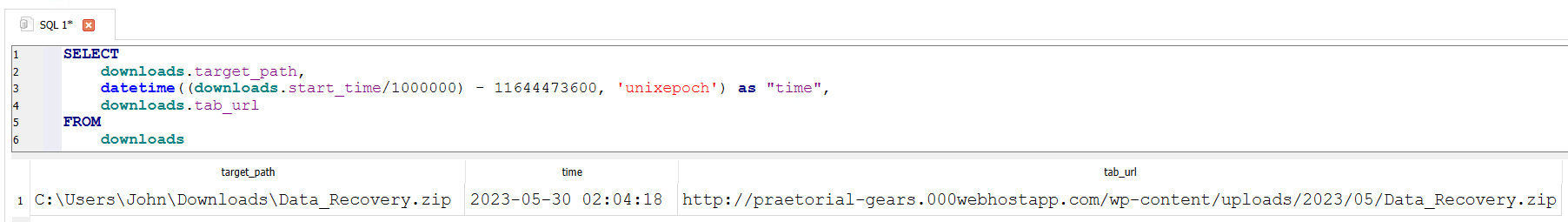
Answer: praetorial-gears.000webhostapp.com
Task 05
Question: The user then executed the suspicious application found in the ZIP archive. What is the process PID?
As already visible in the screenshot for Task 03, the archive contains a Recovery_Setup.exe file. Thanks to this information, the corresponding process and related data can be quickly located in the memory image mounted via MemProcFS, allowing the process ID to be determined.
Select-String -Path "M:\sys\proc\proc.txt" -Pattern "Recovery_Setup"
M:\sys\proc\proc.txt:133:---- Recovery_Setup 484 60 32 U* John 2023-05-30 02:07:59 UTC ***
Caution with this method: the process overview in the proc.txt file truncates image names if they are too long (or too deeply nested) to maintain readability. For double verification, the more detailed overview in the file proc-v.txt can be used. It also provides additional information about the process and its child processes.
---- Recovery_Setup 484 60 32 U* John \Device\HarddiskVolume3\Users\John\Downloads\Data_Recovery\Recovery_Setup.exe
C:\Users\John\Downloads\Data_Recovery\Recovery_Setup.exe
"C:\Users\John\Downloads\Data_Recovery\Recovery_Setup.exe"
2023-05-30 02:07:59 UTC -> ***
High
Answer: 484
Task 06
Question: What is the full path of the suspicious process?
This becomes evident from the additional information in proc-v.txt obtained in the previous Task 05.
Answer: C:\Users\John\Downloads\Data_Recovery\Recovery_Setup.exe
Task 07
Question: What is the SHA-256 hash of the suspicious executable?
This executable can, for example, also be obtained by exporting it from disk_artifacts.ad1. Afterwards, a checksum can be generated to verify that the export is complete and error-free.
Get-FileHash .\Recovery_Setup.exe | Select-Object Hash
Hash
----
C34601C5DA3501F6EE0EFCE18DE7E6145153ECFAC2CE2019EC52E1535A4B3193
Answer: C34601C5DA3501F6EE0EFCE18DE7E6145153ECFAC2CE2019EC52E1535A4B3193
Task 08
Question: When was the malicious program first executed?
From the previous output in Task 05, the execution time 2023-05-30 02:07:59 is already known; however, this executable appears to have been run at least once before. For this, PECmd can be run on the exported Prefetch folder to obtain a timeline of executions.
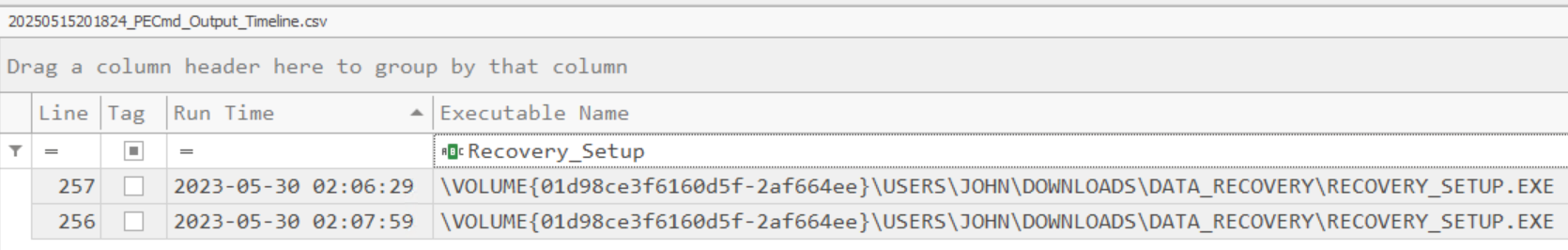
Answer: 2023-05-30 02:06:29
Task 09
Question: How many times in total has the malicious application been executed?
This is also confirmed by the output shown previously in Task 08.
Answer: 2
Task 10
Question: The malicious application references two .TMP files, one is IS-NJBAT.TMP, which is the other?
In the previously mentioned proc-v.txt, besides the already known process with PID 484, there is also a background task (PID: 2732) that lists the known malicious Recovery_Setup.exe installer as its path. This process also has another child process with PID 1764, which is another .tmp file spawned from %LocalAppData%\Temp, similar to the other known process.
---- backgroundTask 2732 60 T * \\Device\\HarddiskVolume3\\Users\\John\\Downloads\\Data_Recovery\\Recovery_Setup.exe
2023-05-30 02:06:27 UTC -> 2023-05-30 02:03:08 UTC
----- is-R7RFP.tmp 1764 2732 T * \\Device\\HarddiskVolume3\\Users\\John\\AppData\\Local\\Temp\\is-T97VD.tmp\\is-R7RFP.tmp
2023-05-30 02:06:35 UTC -> 2023-05-30 02:07:50 UTC
Answer: is-R7RFP.tmp
Task 11
Question: How many of the URLs contacted by the malicious application were detected as malicious by VirusTotal?
By checking the known checksum from Task 07 via VirusTotal, this question can be answered:
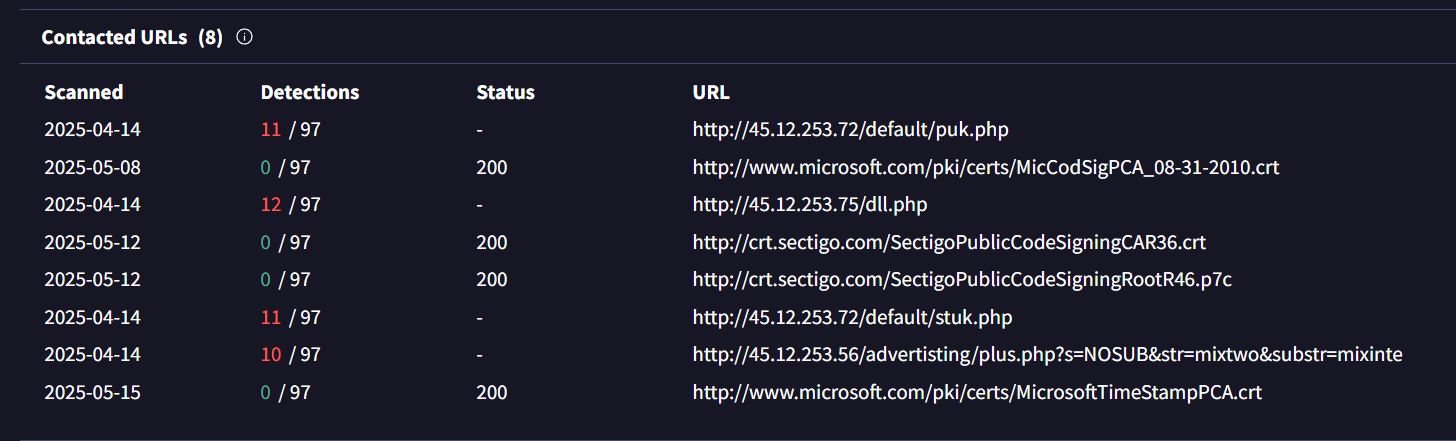
Answer: 4
Task 12
Question: The malicious application downloaded a binary file from one of the C2 URLs, what is the name of the file?
From the contacted URLs list in Task 11 on VirusTotal, multiple files and an IP (45.12.253.72) are visible as part of the C2 communication. At this point the previously mentioned network.pcapng file is helpful: it provides insight into the clients network traffic at the relevant time. By filtering for the known IP and using the HTTP protocol (ip.addr == 45.12.253.72 and http), four GET requests can be identified that match the known pattern.
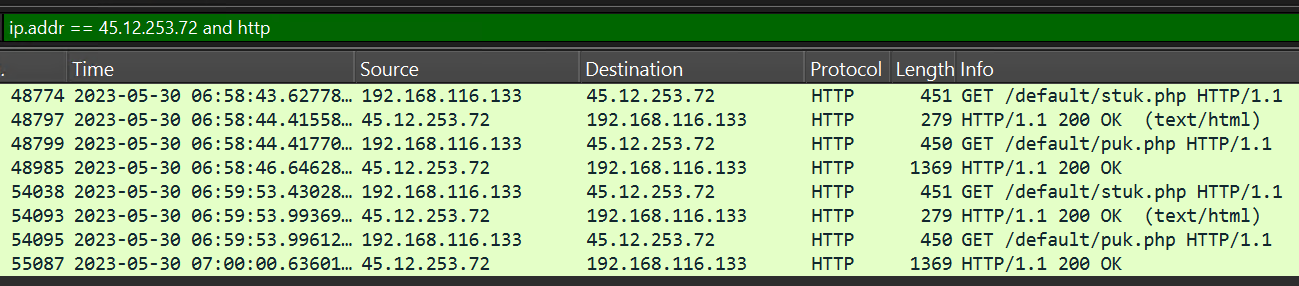
The two requests to /default/stuk.php are answered with a text/html response.
HTTP/1.1 200 OK
Date: Tue, 30 May 2023 06:58:44 GMT
Server: Apache/2.4.41 (Ubuntu)
Content-Length: 21
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8
kvQoRqtcCyMtHmQyQXOUu
However, the subsequent requests to /default/puk.php are responded to with blob binary data that appears to be an encrypted DLL.
HTTP/1.1 200 OK
Date: Tue, 30 May 2023 06:58:44 GMT
Server: Apache/2.4.41 (Ubuntu)
Pragma: public
Expires: 0
Cache-Control: must-revalidate, post-check=0, pre-check=0
Cache-Control: private
Content-Disposition: attachment; filename="fuckingdllENCR.dll";
Content-Transfer-Encoding: binary
Content-Length: 95248
Keep-Alive: timeout=5, max=99
Connection: Keep-Alive
Content-Type: application/octet-stream
The requests to 45.12.253.75 for dll.php, also visible in VirusTotal, are indeed present in the network traffic. However, the server always responds with a 0 response, so no binary is transmitted. For the answer to the task, the requested information is not the filename fuckingdllENCR.dll provided here, but the last part of the URI.
Answer: puk.php
Task 13
Question: Can you find any indication of the actual name and version of the program that the malware is pretending to be?
There are several ways to answer this question. The easiest, fastest and safest is to use public sandboxes and inspect the artifacts produced after executing the file. You can, for example, use the Interactive analysis on ANY.RUN. In the file artifacts there you can find a Readme.txt after a successful installation of the tool that references the original tool name and version.
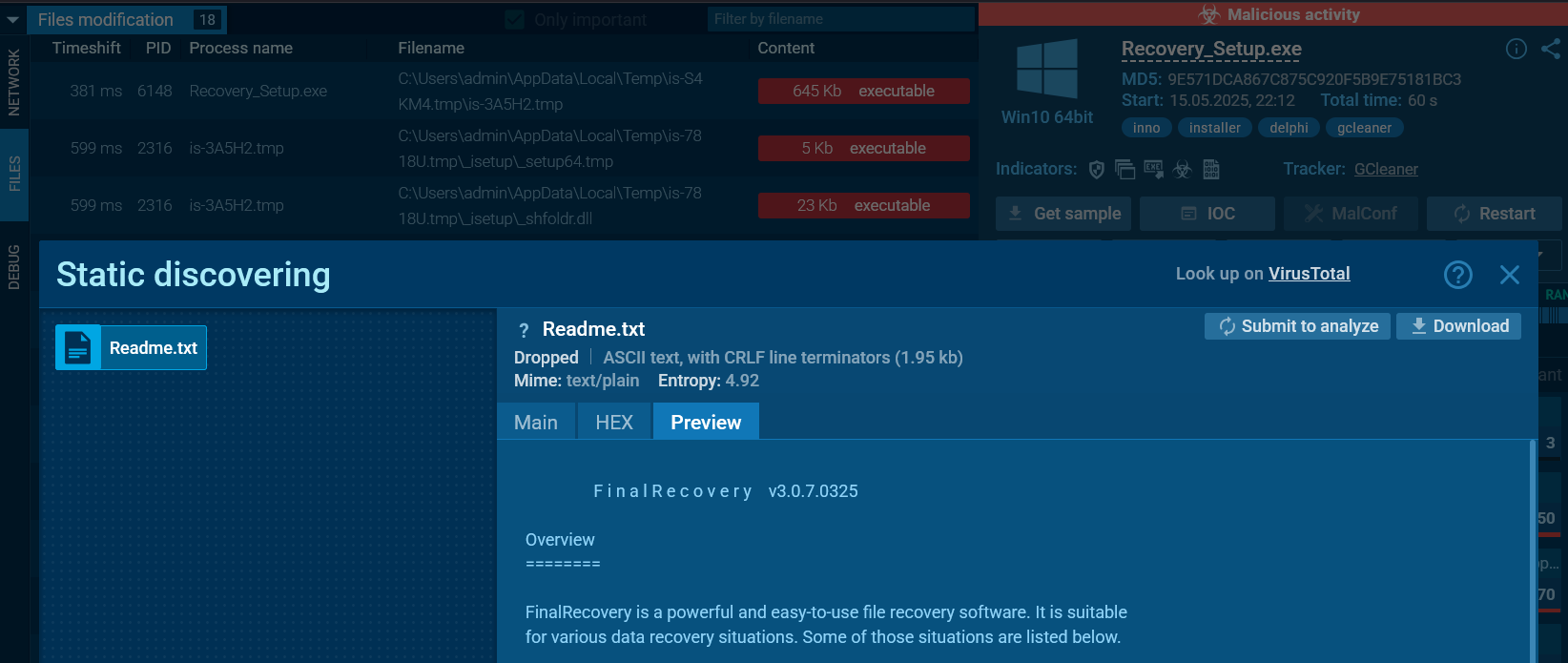
To obtain this file locally (without uploading it to a public sandbox) you can either install it directly, which will extract and execute its files, or, to avoid execution and the associated risk of compromising the system, you can extract the Recovery_Setup.exe. According to the manifest, this is a setup application created with Inno Setup. It therefore contains files that can be extracted and instructions for additional commands and procedures to install them. For this purpose you can generally use, for example, innoextract. However, when running it a hurdle becomes apparent:
.\innoextract.exe --extract .\Recovery_Setup.exe
Extracting "Cov 1.0.5.28" - setup data version 5.1.2
Warning: Setup contains encrypted files, use the --password option to extract them
- "app\Rec528.exe" - encrypted
- "app\finalrecovery.chm" - encrypted
- "app\Readme.txt" - encrypted
- "app\Preview.exe" - encrypted
- "app\data\Config.xml" - encrypted
Done with 1 warning.
A password is required to extract the files. This password is currently unknown to us and therefore must be recovered. Fortunately, this is a well-known and frequently occurring problem, so the associated Git repository contains several issues and pull requests with solutions. The pull request #167 was used which integrates the commit by phcoder and thereby introduces a --code option to extract the compiled code that contains the password.
./innoextract --code Recovery_Setup.exe
Extracting compiled code "Cov 1.0.5.28" - setup data version 5.1.2
Done.
Afterwards, the generated compiled_code.bin can be searched for plaintext strings using strings. One of those strings is the password used to extract the archive.
strings .\compiled_code.bin
Strings v2.54 - Search for ANSI and Unicode strings in binary images.
Copyright (C) 1999-2021 Mark Russinovich
Sysinternals - www.sysinternals.com
[...]
c852bec2d86fa640f8346321
This password can then be used with the --password option to successfully extract the contained files without executing them.
./innoextract --extract ./Recovery_Setup.exe --password c852bec2d86fa640f8346321
Extracting "Cov 1.0.5.28" - setup data version 5.1.2
- "app/Rec528.exe"
- "app/finalrecovery.chm"
- "app/Readme.txt"
- "app/Preview.exe"
- "app/data/Config.xml"
Done.
An inspection of the Readme.txt shows the same output already produced during the public sandbox run.
Get-Content -Path '.\Readme.txt'
F i n a l R e c o v e r y v3.0.7.0325
[...]
Answer: FinalRecovery v3.0.7.0325
Appendix
A closer look into the extracted compiled_code.bin file, made possible through a visual inspection using HxD, reveals that it appears to be a Pascal Script file. According to the relevant Wikipedia article, such scripts are a well-known component of Inno Setup installers.
There are various tools to parse or decompile these files, since they are often used in a malware context and analysis is therefore frequently necessary. An example used to generate the pseudo-sources is IFPSTools.NET, a tool by Wack0 / Rairii which provides (via ifpsdasm) a wrapper around the IFPSLib disassembler functionality which was ported from original. After a successful decompile, you can inspect the pseudo‑code representation of the object used by the Inno Setup installer. For example, various imports from external DLLs become visible.
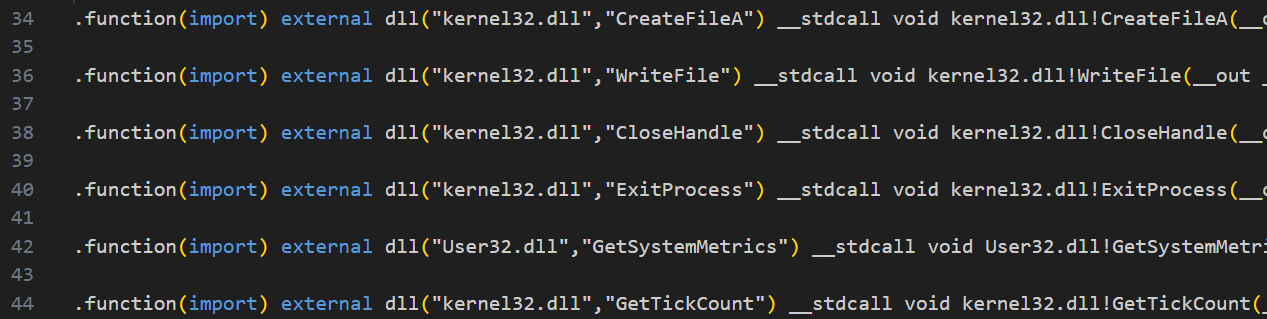
Particularly important for decrypting the files and for the installer’s further behavior is the INITIALIZESETUP() function. This is the function, according to the relevant documentation, called by Inno Setup for initialization. The decompiled source also contains INITIALIZEWIZARD(), which is likewise a function covered in the Pascal Scripting Setup event functions. Additionally, there are MEETSOFTFROPEN, MEETSOFTFRINSTALL, and MEETSOFTFRCLOSE. A Google search reveals that these last three functions apparently have cross-references to other (real) malware samples.
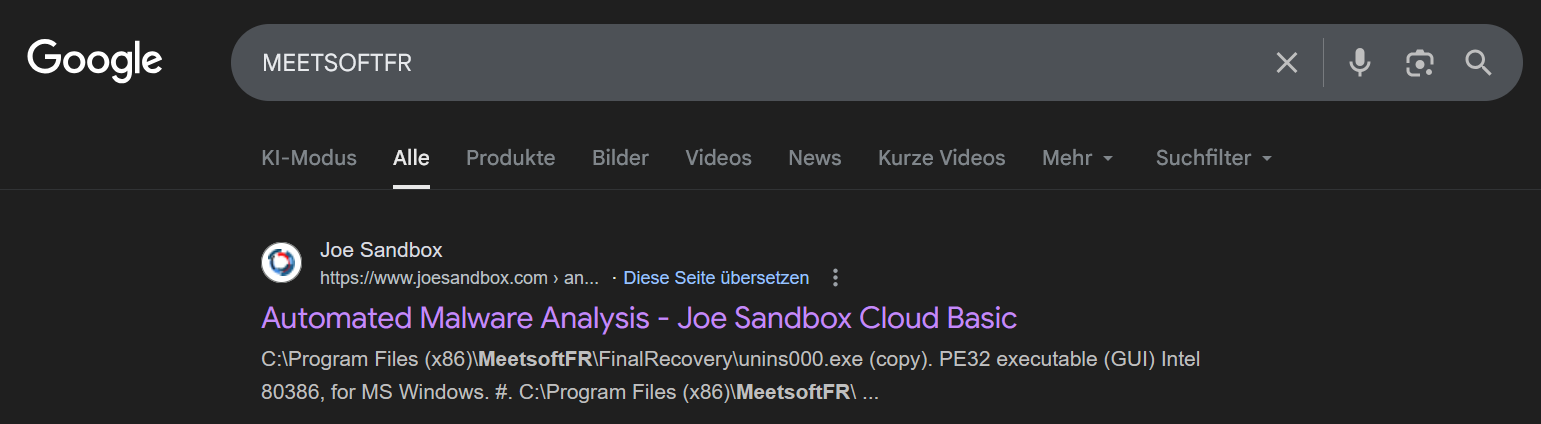
The first result leads to a report on JOESandbox for the sample (SHA256: c9abeb237b284d2aee39f0c69a1042aa3dbe285aa528f23ffdaed82a0a08a229), where MeetsoftFR is used as part of the path into which the program is installed. When testing this sample, exporting its compiled source and decompiling it revealed that the same password was used, so the sample could also be extracted revealing another malicious payload which dynamically loads multiple different stealers and executes them.
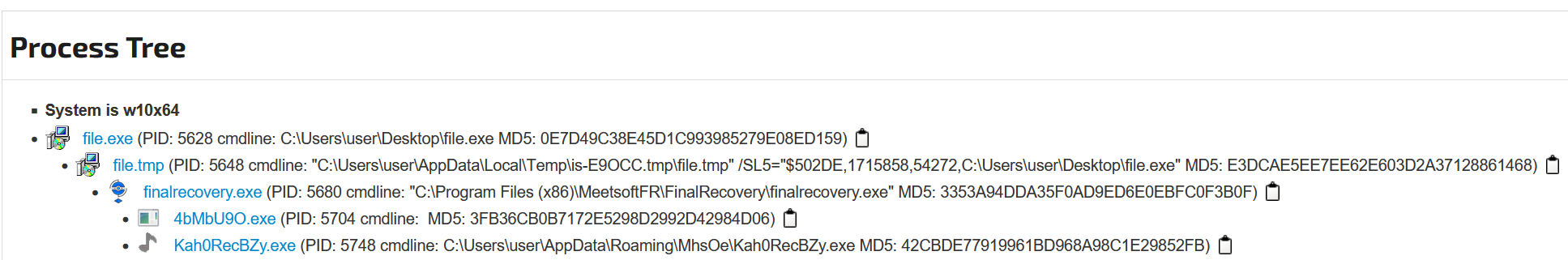
Additionally, the rest of the decompiled code is very similar, so the three highly specific functions with the well-known MEETSOFTFR naming convention are also recognizable. This reveals an overlap between the two samples and their authors. Apparently, both samples were created around the same time and were not clearly separated. While both samples use the function names within this naming scheme, the public sample also has this directory in the path where it is deployed, whereas the Sherlock sample, although sharing the same function names, is installed in the FLSCover folder.
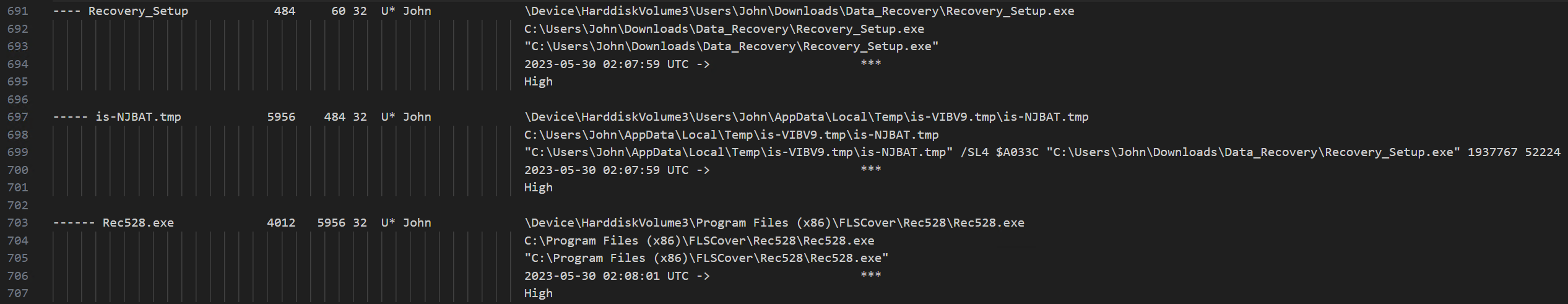
Within the two initialization functions, several additional activities, likely anti-analysis measures, are executed before the actual extraction. For example, a FINDWINDOWBYWINDOWNAME call checks whether a window with the specific name r2e391_FLSCover528Class_r2e391 already exists, presumably to prevent multiple executions. Next, a global variable is initialized with 2c85bedc286ffa6408324631 and then checked via CHECKFORMUTEXES to see if it already exists. There are also two calls to the GetTickCount() function to measure the time interval between executions, likely to detect potential analysis. If all checks pass, a global variable for the password (as previously inferred in Task 13 using strings) is set to c852bec2d86fa640f8346321, which is then used in the INITIALIZEWIZARD() function to allow successful extraction.