compromised
 | Released | 2024-11-21 |
| Retired | 2025-05-15 | |
| Author | abdelrhman322 |
Scenario
Task 01
Question: What is the IP address used for initial access?
In this case, only the capture.pcap file is available for analysis of the incident. This is a packet capture file used to store raw network traffic data, allowing the entire network traffic during the recording period to be reconstructed and reviewed. The recording started on May 17, 2023 at 15:32:04 (UTC) and includes all packets (39.106 in total) up to 18:06:49 UTC.
To get a better overview of the contents of the capture, it helps to take a look at Statistics > Conversations in the Wireshark menu.
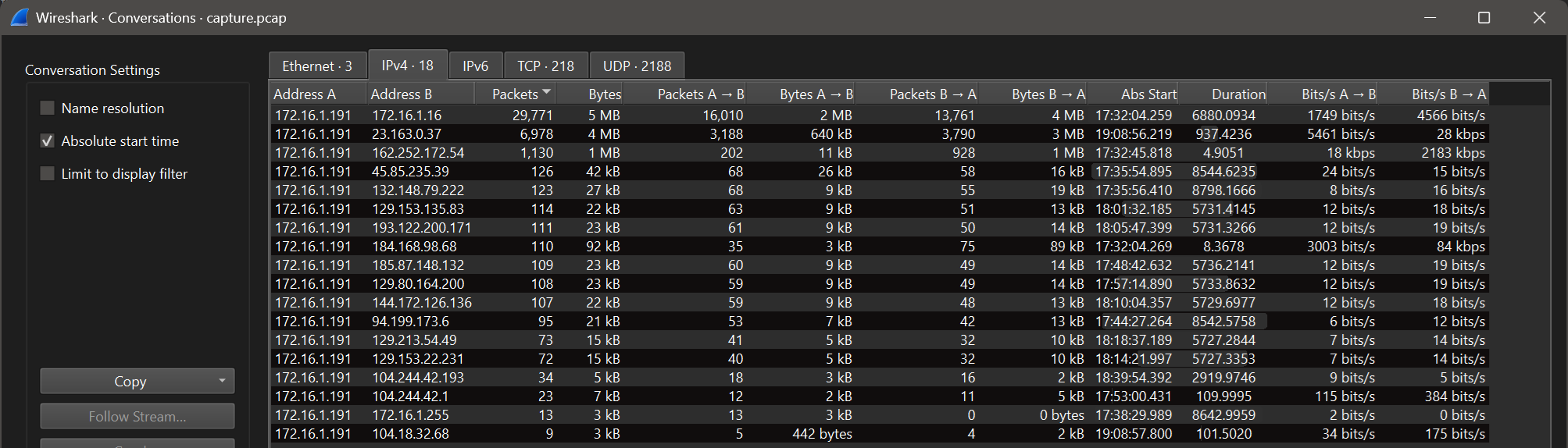
This overview shows: the traffic was captured for the 172.16.1.191 machine, the partner that received most of the traffic was another local host (.16), and with the third most frequent conversation partner, significantly more packets and bytes were sent to the host system than to the destination. This suggests the download of a larger file, as only a few requests generated a lot of response traffic. This is confirmed by checking the Statistics > HTTP > Requests view - during the capture period, only 2 files were transferred via HTTP, one of them with a suspiciously random file name and path, and from the IP address that was already noticeable in the first statistics.
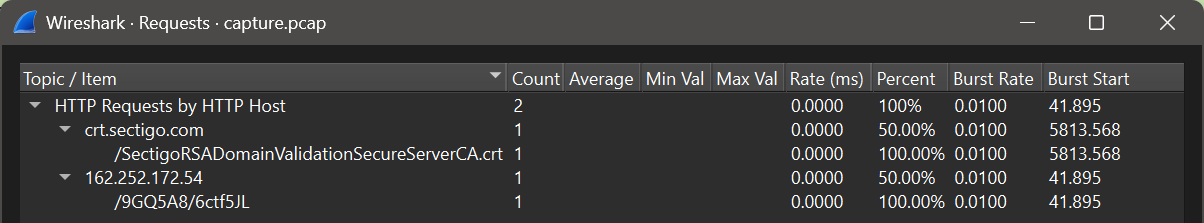
These two indications alone are only sufficient for a suspicion of the correct answer for this task. However, through later tasks and insights gained from the analysis of the downloaded file, this suspicion will become clearer.
Answer: 162.252.172.54
Task 02
Question: What is the SHA256 hash of the malware?
Assuming that the previously identified file is the described malware, this file can be reconstructed and exported from the traffic. Afterwards, the hash can be determined.
Get-Filehash .\6ctf5JL | Select-Object Hash
Hash
----
9B8FFDC8BA2B2CAA485CCA56A82B2DCBD251F65FB30BC88F0AC3DA6704E4D3C6
Answer: 9B8FFDC8BA2B2CAA485CCA56A82B2DCBD251F65FB30BC88F0AC3DA6704E4D3C6
Task 03
Question: What is the Family label of the malware?
Thanks to the export of the malware and the determined hash, a platform like VirusTotal can be used to easily initiate further investigations or review past results. The multi-scanning also reveals the malware family.
Answer: Pikabot
Task 04
Question: When was the malware first seen in the wild (UTC)?
The details tab at VirusTotal reveals the First Seen In The Wild timestamp.
Answer: 2023-05-19 14:01:21
Task 05
Question: The malware used HTTPS traffic with a self-signed certificate. What are the ports, from smallest to largest?
To answer this question, the CLI tool tshark can be used. It allows quick and easy filtering of various fields in network packets to gain a good overview. To identify HTTPS traffic, the filter "tls.handshake.type == 11" is set using the -Y flag, and then the fields tcp.srcport and x509ce.dNSName are read. According to the documentation, this field contains the DNS name associated with the used x509 certificate.
tshark -r capture.pcap -Y "tls.handshake.type == 11" -T fields -e tcp.srcport -e x509ce.dNSName | sort | uniq
2078
2222
32999
443 twitter.com,www.twitter.com
443 webmasterdev.com,autodiscover.webmasterdev.com,cpanel.webmasterdev.com,mail.webmasterdev.com,webdisk.webmasterdev.com,webmail.webmasterdev.com,www.webmasterdev.com
Three ports stand out here where apparently no DNS name is recorded (or it cannot be read). Additionally, it is noticeable that for hits on port 443 legitimate domain names are present. For a more detailed investigation, the uTF8String attribute of the x509sat can also be read - this again reveals suspiciously random data for the three already suspicious ports:
tshark -r capture.pcap -Y "tls.handshake.type == 11" -T fields -e tcp.srcport -e x509sat.uTF8String | sort | uniq
2078 AC,Marginellidae Cogitabundous Inc.,Unallowedly Nonmedicative,Etymography,formamide.ruhr,AC,Marginellidae Cogitabundous Inc.,Unallowedly Nonmedicative,Etymography,formamide.ruhr
2078 EN,Awarrant,Prediet,Wrinkles Fireless,nonveracitygalvanometry.band,EN,Awarrant,Prediet,Wrinkles Fireless,nonveracitygalvanometry.band
2078 KI,Uneared Inc.,Undelightful,Pyopneumopericardium,votation.bzh,KI,Uneared Inc.,Undelightful,Pyopneumopericardium,votation.bzh
2078 ST,Compete Disminister,Gulfed,Boschbok,ancylopodaphonoscope.live,ST,Compete Disminister,Gulfed,Boschbok,ancylopodaphonoscope.live
2222 BR,Hayburner Inc.,Uncontestablely,Henwise Chirotonsory,organizabilitybigate.rehab,BR,Hayburner Inc.,Uncontestablely,Henwise Chirotonsory,organizabilitybigate.rehab
2222 RE,Komsomol,Melaniline,Simonists Kustenau,unsucculent.earth,RE,Komsomol,Melaniline,Simonists Kustenau,unsucculent.earth
2222 UN,Anaudia Aquose Inc.,Halutz,Priorship,lordless.name,UN,Anaudia Aquose Inc.,Halutz,Priorship,lordless.name
32999 CA,Lapins Aerobacteriological Inc.,Inappellable,Turgidities,istiophoridaecummer.date,CA,Lapins Aerobacteriological Inc.,Inappellable,Turgidities,istiophoridaecummer.date
32999 DE,Enmeshing Inc.,Reasseverate,Hitchhiking Sustentational,tennesseealkamine.me,DE,Enmeshing Inc.,Reasseverate,Hitchhiking Sustentational,tennesseealkamine.me
443
443 Greater Manchester,Salford,Comodo CA Limited,AAA Certificate Services
Answer: 2078, 2222, 32999
Task 06
Question: What is the id-at-localityName of the self-signed certificate associated with the first malicious IP?
For the usage of the previously found certificates and the association to the IP as well as the extraction of further information about the certificate, either Wireshark or the verbose mode of tshark can be used. For visualization, the display filter tls.handshake.type == 11 is applied again, and then the first frame, not using the twitter, nor the webmaster dev certificate, (1249 at 15:35:55 UTC) is examined.
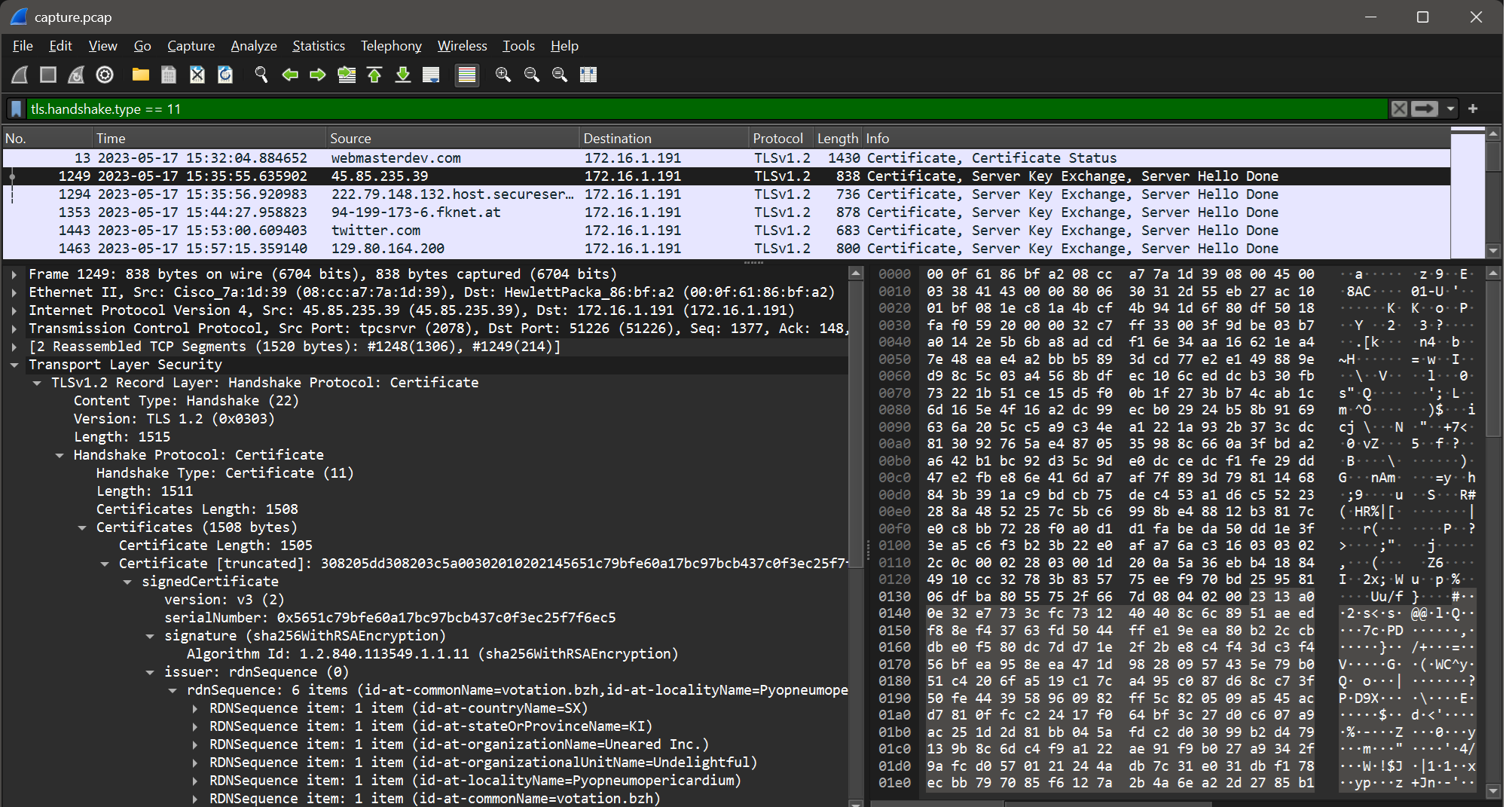
Answer: Pyopneumopericardium
Task 07
Question: What is the notBefore time(UTC) for this self-signed certificate?
This information can also be read from the output of Wireshark or tshark for the certificate.
signedCertificate
version: v3 (2)
serialNumber: 0x5651c79bfe60a17bc97bcb437c0f3ec25f7f6ec5
signature (sha256WithRSAEncryption)
issuer: rdnSequence (0)
validity
notBefore: utcTime (0)
utcTime: 2023-05-14 08:36:52 (UTC)
notAfter: utcTime (0)
utcTime: 2024-05-13 08:36:52 (UTC)
subject: rdnSequence (0)
rdnSequence: 6 items
RDNSequence item: 1 item (id-at-countryName=SX)
RDNSequence item: 1 item (id-at-stateOrProvinceName=KI)
RDNSequence item: 1 item (id-at-organizationName=Uneared Inc.)
RDNSequence item: 1 item (id-at-organizationalUnitName=Undelightful)
RDNSequence item: 1 item (id-at-localityName=Pyopneumopericardium)
RDNSequence item: 1 item (id-at-commonName=votation.bzh)
Answer: 2023-05-14 08:36:52
Task 08
Question: What was the domain used for tunneling?
To answer this question, a more detailed look at the dataset is required. When reviewing the protocols present, it becomes noticeable that there is an unusually large amount of DNS traffic.
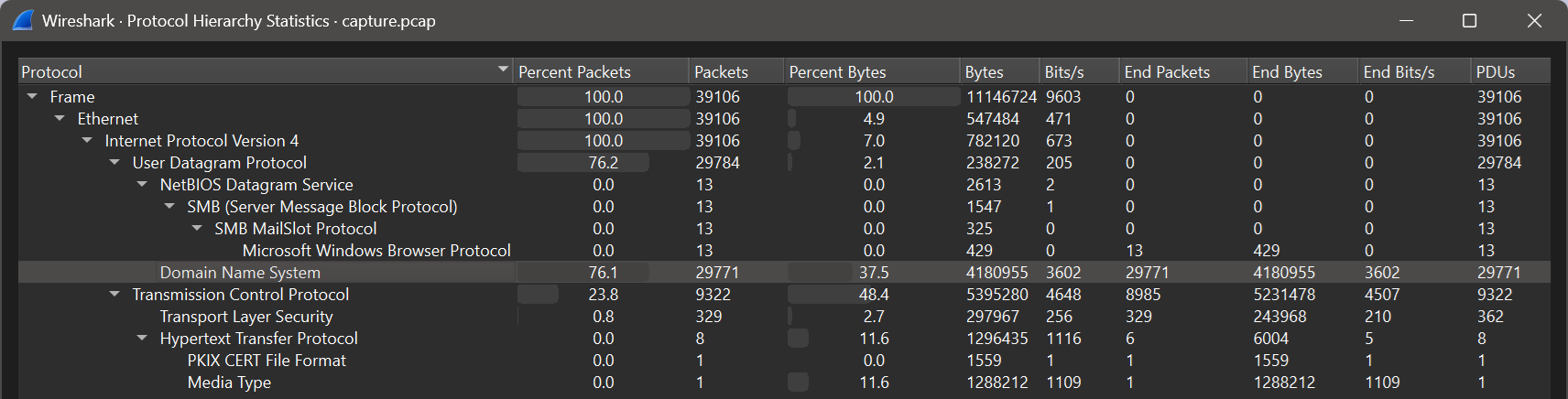
In a quick visual inspection of the DNS entries in Wireshark, it quickly becomes clear that a form of DNS tunneling is being used to send commands to the infected endpoint or extract responses. To identify this domain, either the result of the visual inspection in Wireshark can be used, or an overview of all DNS requests can be obtained using a short Scapy Python script, allowing a clear outlier to be identified as malicious C2.
from scapy.all import rdpcap, DNS, DNSQR, IP
from collections import Counter
packets = rdpcap('./capture.pcap')
domain_counter = Counter()
for packet in packets:
if packet.haslayer(DNS) and packet.haslayer(IP):
dns_layer = packet[DNS]
if dns_layer.qd:
queried_name = dns_layer.qd.qname.decode('utf-8').rstrip(".")
queried_name = ".".join(queried_name.split(".")[-2:]).rstrip(".")
domain_counter[queried_name] += 1
print("DNS Request Counts by Domain:")
for domain, count in domain_counter.items():
print(f"{domain}: {count}")
# DNS Request Counts by Domain:
# webmasterdev.com: 2
# twitter.com: 7
# steasteel.net: 29758
# gitinab.xyz: 2
# sectigo.com: 2
Through this IoC, further OSINT searches for the malware and domains used can be initiated, allowing more information about the campaign to be gathered. This verifies all of our findings.
Answer: steasteel.net